 Microsoft have now released Microsoft Security Essentials 2.0 to the web which has a number of new features over the previous version.
Microsoft have now released Microsoft Security Essentials 2.0 to the web which has a number of new features over the previous version.
- Windows Firewall integration – During setup, Microsoft Security Essentials will now ask if you would like to turn the Windows Firewall on or off.
- Enhanced protection for web-based threats – Microsoft Security Essentials now integrates with Internet Explorer to provide protection against web-based threats.
- New protection engine – The updated anti-malware engine offers enhanced detection and cleanup capabilities with better performance.
- Network inspection system* – Protection against network-based exploits is now built in to Microsoft Security Essentials.
Therefore I have updated my previous post based Group Policy for Microsoft Security Essentials to support configuring the newly added features.
If you want more general info about MSE v2 see: Security Garden: Microsoft Security Essentials 2.0 Released
If you want to download it visit http://www.microsoft.com/downloads/en/details.aspx?FamilyID=e1605e70-9649-4a87-8532-33d813687a7f
Before I begin I should remind you that Microsoft only allows MSE to be used for free in small businesses with less that 10 seats (see here). But MSE does not natively support Group Policy and having to configured even 10 copies of Microsoft Security Essentials (MSE) manually can be a pain. So the instructions below is simply a way to configure the registry keys of the application using the Group Policy Preferences Registry key setting.
Tip: If the below instructions to create the registry keys seems like to much work you will be glad to know that I have put a link at the bottom to an XML Group Policy Preferences Registry file. You can use this file to import the all the Policy Registry setting I talk about below automatically.
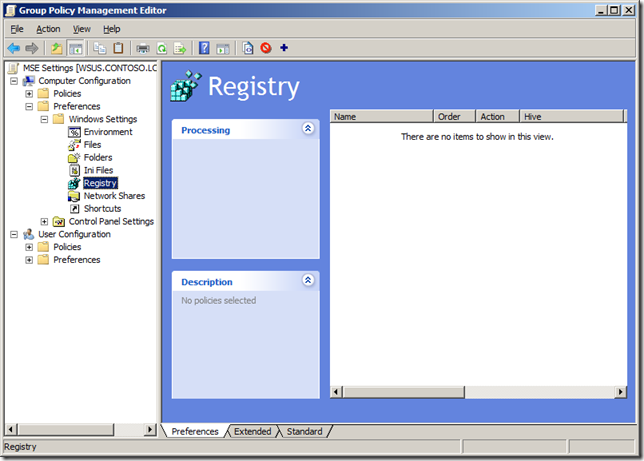
How to use Group Policy Preferences Registry key setting.
Before we begin we first need to know how to create a Group Policy Preferences Registry Key setting that we will use to control each of the registry keys we need to configured MSE. The following steps will need to be repeated for each registry key below.
Step 1. Edit a Group Policy Object that is applied to the computers you want this setting applied.
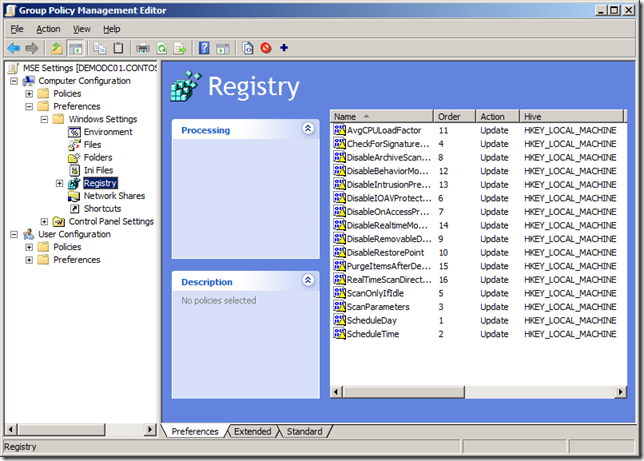
Step 2. Navigate to Computer Configuration > Preferences > Windows Settings > Registry
Step 3. In the Menu click on Action > New > Registry Item
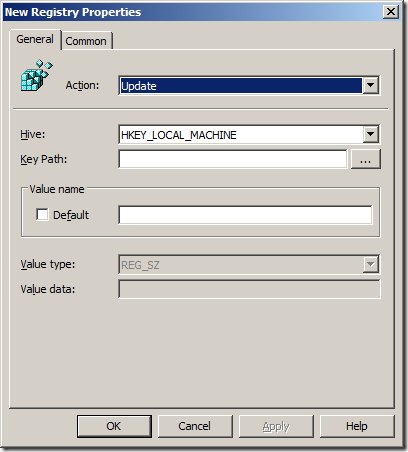
Now you know how to configure a registry key setting using Group Policy Preferences you can create a new Registry Item for each registry key listed below.
Note: The Data values below that are highlighted in BOLD are the values you need to use to replication the examples shown.
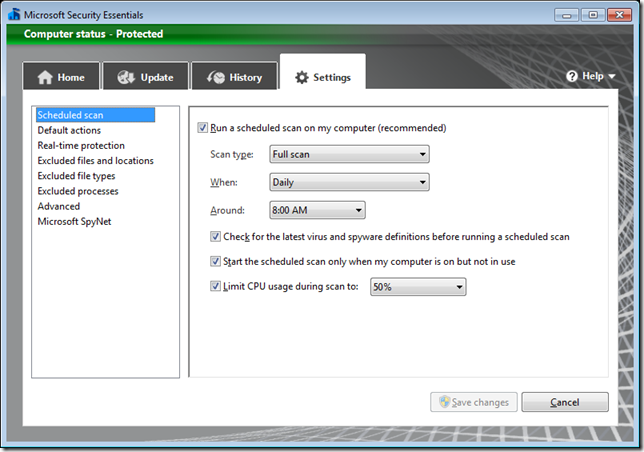
How to configured Scheduled Scan using Group Policy for Microsoft Security Essentials
Now you need to create a registry few specific registry keys. In this example we are going to configured a Full Scheduled scan to run each day at 8am. We are also going to enable the option to check for an update before scanning and we are going to configure the scan to
Scheduled Day
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Scan
Value: ScheduleDay (REG_DWORD)
Data: 0 (Every Day)
Data: 1 (Sunday)
Data: 2 (Monday)
Data: 3 (Tuesday)
Data: 4 (Wednesday)
Data: 5 (Thursday)
Data: 6 (Friday)
Data: 7 (Saturday)
Scheduled Time
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Scan
Value: ScheduleTime (REG_DWORD)
Data: 0 (12am)
Data: 000001e0 (8am)
The data of this value represents the number of minutes from 12am in hex… therefore if you want 8am configured the data to “000001e0â€
Full or Quick Scan
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Scan
Value: ScanParameters (REG_DWORD)
Data: 1 (Quick Scan)
Data: 2 (Full Scan)
Check for Update before scanning
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Scan
Value: CheckForSignaturesBeforeRunningScan (REG_DWORD)
Data: 0 (Disabled)
Data: 1 (Enabled)
Scan only when idle
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Scan
Value: ScanOnlyIfIdle (REG_DWORD)
Data: 0 (Scan when idle)
Data: 1 (Scan when active)
Limit CPU Usage
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Scan
Value: AvgCPULoadFactor (REG_DWORD)
Data (Decimal): 10 (10%)
Data (Decimal): 50 (20%)
Data (Decimal): 90 (90%)
Now all your computers will have the scheduled scan option configured as the following image below.
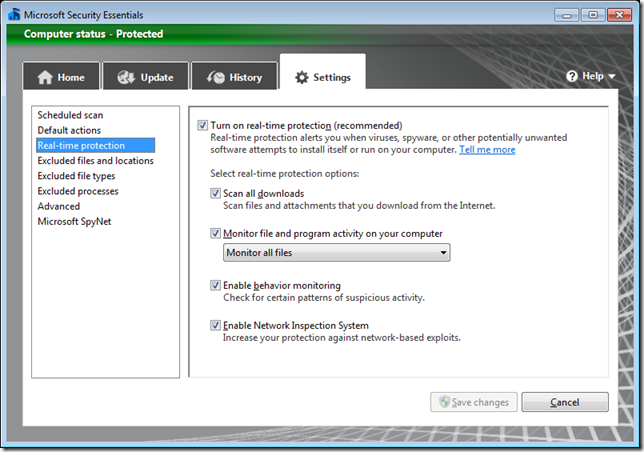
How to configure Real-Time Protection options using Group Policy for Microsoft Security Essentials
Below are the registry keys for configuring the “Rea-Time Scanning†settings for Microsoft Security Essentials.
Monitor file and program activity
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Real-Time Protection
Value: DisableIOAVProtection (REG_DWORD)
Data: 0 (Real-Time scan Enabled)
Data: 1 (Real-Time scan Disabled)
Scan all downloaded files and attachments
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Real-Time Protection
Value: DisableOnAccessProtection (REG_DWORD)
Data: 0 (Scan Enabled)
Data: 1 (Scan Disabled)
Scan all downloaded files and attachments
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Real-Time Protection
Value: DisableOnAccessProtection (REG_DWORD)
Data: 0 (Scan Enabled)
Data: 1 (Scan Disabled)
Disabled Real Time Monitoring
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Real-Time Protection
Value: DisableRealtimeMonitoring(REG_DWORD)
Data: 0 (Scan Enabled)
Data: 1 (Scan Disabled – but why would you want to disable it…?)
Disabled Intrusion Prevention System
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Real-Time Protection
Value: DisableIntrusionPreventionSystem(REG_DWORD)
Data: 0 (IPS Enabled)
Data: 1 (IPS Disabled)
Real Time File Scanning Direction
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Real-Time Protection
Value: DisableIntrusionPreventionSystem(REG_DWORD)
Data: 0 (Both)
Data: 1 (Incoming)
Data: 2 (Outgoing)
You real time protection should now be configured as shown below.
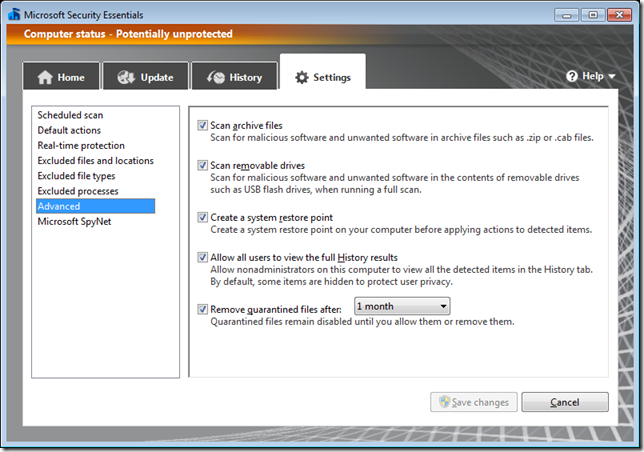
How to configure Advanced Real-Time Protection options using Group Policy for Microsoft Security Essentials
Below are the registry keys for configuring the “Advanced†settings for Microsoft Security Essentials.
Scan archive files
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Scan
Value: DisableArchiveScanning (REG_DWORD)
Data: 0 (Enable Archive Scanning)
Data: 1 (Disable Archive Scanning)
Scan Removable Drives
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Scan
Value: DisableRemovableDriveScanning (REG_DWORD)
Data: 0 (Scan Enabled)
Data: 1 (Scan Disabled)
Create a system restore point
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Scan
Value: DisableRestorePoint (REG_DWORD)
Data: 0 (Create Restore Point)
Data: 1 (Do not create Restore Point)
Remove Quarantine file after (x days):
Key: HKLM\Software\Microsoft\Microsoft Antimalware\Quarantine
Value: PurgeItemsAfterDelay (REG_DWORD)
Data (Decimal): 30 (30 Days)
Importing Group Policy Preferences
For your convenience I have provided you a link to a XML Group Policy Preferences Registry file for all the above settings.
Or here https://www.grouppolicy.biz/wp-content/uploads/2010/MSE_Settings_2.xml if the link on the image above does not work.
Simply save the file to your desktop and then drag it into the empty pane on the right hand side, click “Yes†to confirm the import and you will have all the registry keys automatically created.




Blog Post: Group Policy for Microsoft Security Essentials 2.0 http://bit.ly/e8Ruce
Updated MSE post http://t.co/Ll0bEeO to include link to MVP Alan Burchill's instructions for Group Policy for MSE 2.0 http://bit.ly/f992JU
The link to XML registry file contains domain name twice 🙂
Nice tutorial. Thanks! 🙂
@edbott Doh.. I blame iPad copy and paste… Here is the right one http://j.mp/gAGEtE
@jamesbannan @edbott yes it is… http://j.mp/gAGEtE
Thank you.
What about proxy configuration ?
@Francois If you can find the registry key that configs proxy for MSE i will make a change.. but i am pretty sure it just uses the proxy config of IE.
Group Policy for Microsoft Security Essentials 2.0 http://t.co/lzXsQIl via @alanburchill
Now that MSE signatures (not engines) can be updated via WSUS, is there a registry setting to point MSE to the appropriate WSUS server? We are in a workgroup environment. WSUS works great for Windows Updates, but MSE is new to us.
My understanding is that configuing the client to use a WSUS server will mean that it will then pull signitature updates from the WSUS server automaticlly…
From what I’m seeing, I’ve got a non-internet connected windows domain with Windows Updates configured to connect to an internal WSUS server. I have Windows 7 64-bit clients that appear to be connecting to my WSUS server from what I’m seeing in the WindowsUpdate.log file, but MSE seems to be stubbornly trying to continue to connect to http://www.update.microsoft.com and failing.
@John Interesting… have you check to see if the update is installing (via update history) on the local computer. MSE may poll windows update directly however WSUS should also be pushing out the pattern update…
I’m trying to import the xml file on Server 208 R2, but I get an error saying that the file is invalid? Any suggestions?
Alan – perhaps a typo. If you search for:
Data (Decimal): 50 (20%)
perhaps you meant 50%?
:=)
Hi. A few minutes ago I have tested the *.xml file and for me it works fine and now all my computers in the laboratory are nice configured. Thanks a lot!!
I have heard more and more interest on this topic. It’s true that technology shape us, it makes new behaviors for the customers, both good and bad. On the other hand, The Roots International Dubai shapes technology only by acknowledging it.
Thank you very much for sharing a great topic
I think, that the key for “Real Time File Scanning Direction” is wrong. In your topic, the same key stands for Disabled Intrusion Prevention System and File Scanning Direction (it is DisableIntrusionPreventionSystem – REG_DWORD). So “RealtimeScanDirection” seems the right key for me.
Nice Write up need to be appreciated http://wiseplayappdownload.com/wiseplay-apk-download-android-phones-tablets/
Nice tutorial. Thanks!
I have heard more and more interest on this topic. It’s true that technology shape us, it makes new behaviors for the customers, both good and bad. On the other hand, The Roots International Dubai shapes technology only by acknowledging it.
Very nice according to it post! Thanks for posting that i was searching about!!
Your website is very interesting, it is very meaningful and inspirational. I think your website deserves to be the number one. hopefully it could be real. Thank you in advance for own variety. I wish all of you is given a long life in order to continue working
Thank you very much for sharing a great topic
Very nice according to it post! Thanks for posting that i was searching about!!