![]() In this article I will show you how to disable the SSL v2 and SSL v3 protocols on the Windows Server so that it no longer offers the depreciated (a.k.a. Broken) SSL v2 and v3 security protocols. It also does not hurt if you apply this policy settings to your Windows client computers in case any of them have IIS with digital certificate enabled.
In this article I will show you how to disable the SSL v2 and SSL v3 protocols on the Windows Server so that it no longer offers the depreciated (a.k.a. Broken) SSL v2 and v3 security protocols. It also does not hurt if you apply this policy settings to your Windows client computers in case any of them have IIS with digital certificate enabled.
Note: That if you are running a non Microsoft web server such as Apache then you will need to contact that vendor for specific instructions on how to disabled the protocol.
In my previous blog post How to disable SSL v2 and SSL v3 on the client via Group Policy I explain why SSL v2 and v3 is bad and I showed you how to disable these protocols on the client. In this post I show you how to disable it in the OS so that the web server, LDAP or any other service that can uses SSL/TLS will only use TLS v1.0 or greater.
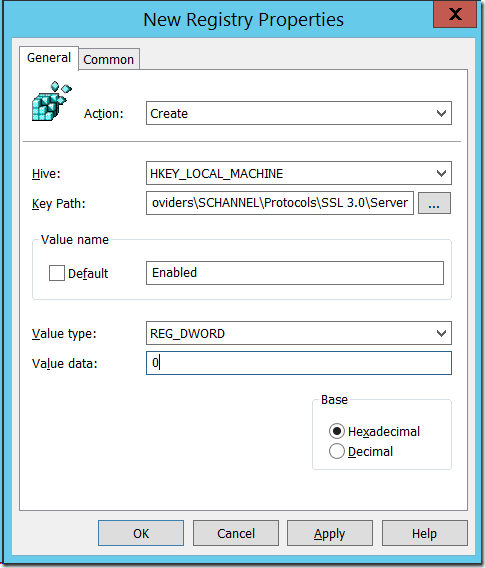
The first step will be to create a Group Policy that is targeted to the servers that you want to disable SSL. Then open up Computer Configuration > Preferences > Windows Settings > Registry. Then create two new “Registry Items†as per follows:
Key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server
Name: Enabled
Value: Reg_Dword 0
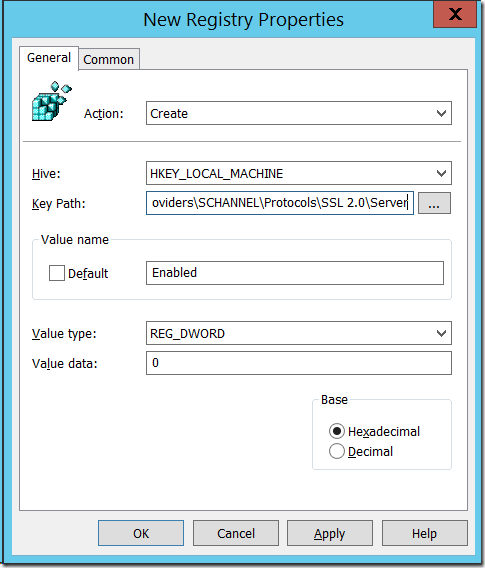
Key: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server
Name: Enabled
Value: Reg_Dword 0
Restart the server and you should now be done.
Alternatively, if your server is not domain joined then you can save the below registry key information as a .Reg file and just manually apply it to your server.
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server] “Enabled”=dword:00000000 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server] “Enabled”=dword:00000000
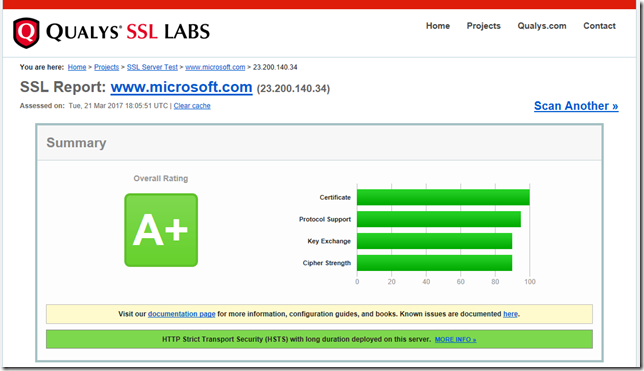
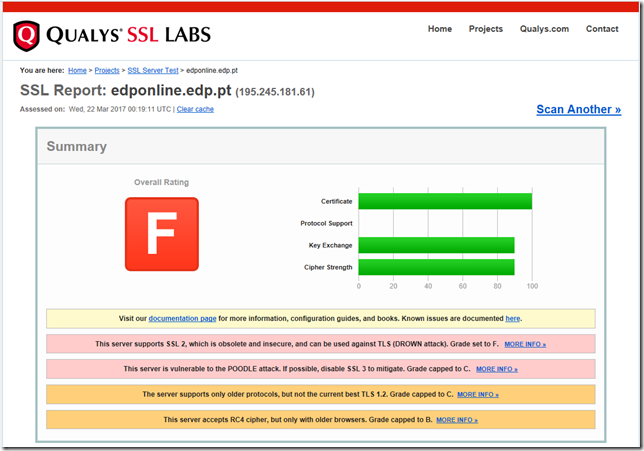
Once you have applied the setting to the server it would be best to reboot to ensure that the setting is properly applied. If you web server is on the internet then you can ensure that is has worked by using the http://ssllabs.com/ web site to perform a test against you site.
As you can see with the examples below, having SSL v2 and v3 enabled can make the world of difference in the of security of your web site.
Additional references: http://disablessl3.com/