In this article I am going to talk about how you can use Group Policy to control the firewall that comes out of the box with Windows but first I want to give you a bit of history of the evolution of host based firewall in Windows. Firewalls have long been around for year protecting internal corporate networks from outside attackers (see image below).
With the explosion of mobile workers in the late 90’s more and more people were connecting their laptops directly to the internet without the benefit of protection of a corporate firewall. As a result back in the early 2000’s third-party firewall products such as ZoneAlarm became a very popular way to security against attacks. Microsoft then added a host based firewall with the release of Windows XP/2003 that was unfortunately turned off by default. As a result of having the firewall turned off by default in there were a number of computer worms of which most notably were the Blaster worm and Sasser worm that spread like wildfire to pretty much any Windows computer that had not been specifically secured.
As a result Microsoft decided to make a major change with how Windows XP was configured with the release of Service Pack 2. When users installed service pack 2 they were now prompted to turn on the firewall thus protecting them from malicious communications. The problem with enabling a firewall however is that you generally block all incoming traffic by default which means product such as Skype and/or Windows Messenger could no longer receive incoming call’s or messages. To get around this issues end users would be prompted when an application wanted to open up a incoming port on the network. Corporate IT staff could control this for the users using Group Policy via the Windows Firewall section under Administrative Templates > Network > Network Connections.
This was a good first step however creating a set of firewall rules using the native group policy setting under Windows Firewall was challenging at best as there most setting had to be configured manually.
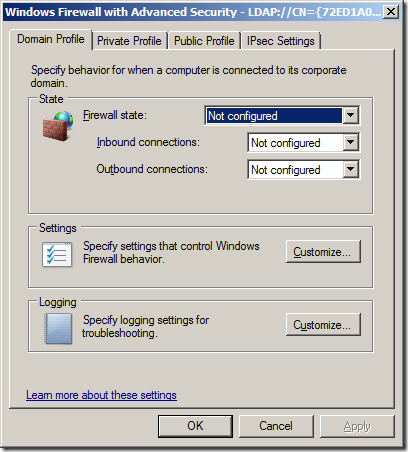
With the release of Windows Vista/2008 Microsoft totally revamped the Windows Firewall to allow for much easier administration. IT Admins now have much more granular control over how they can manage the firewall rules and they now have the ability to control both inbound and outbound communication as well as being able to selective enable rules depending on what network the computer is connected. They also changed where you configured the firewall via group policy to Windows Settings > Security Settings > Windows Firewall with Advanced Security which has enable some cool features such as importing and exporting firewall rules which I will go into later.
Below I will go though an example of a IT administrator wanting to setup a default set of firewall rules for a Windows 7 laptop computers and with a rule to allow Skype when connected at home and on the Internet but not when connected to the domain. Normally in the real world you would have many more inbound exceptions however you should be able to use this as a guide to get you started to build your firewall rule setup specifically for your environment.
Before you begin: If you have already configured firewall setting under the older “Windows Firewall†section these policy rule will also apply and the two rule sets will try to merge with unpredictable results. I recommend that you make sure that no “Windows Firewall†setting are applied to your Vista/2008 or greater computers and that you solely apply the firewall setting to these newer computers via the “Windows Firewall with Advanced Security†group policy security option.
Configuring Windows Firewall Rule
First we will setup a reference computer with the firewall rule the way we want and then explore them so we can import them into a group policy. Configuring the firewall rules on the PC first gives us an opportunity to properly test the rules before deploying them to other computers. If also allows us to export all the rules in one action so that you don’t have to go through the lengthy process of setting up all the rules manually one by one.
In this example this computer is running Windows 7 and already has Skype 4.2 installed.
Step 1. Right click on the network status icon in the system tray and click on "Open Network and Sharing Centerâ€
Step 2. Click on “Windows Firewall†in the lower left hand corner.
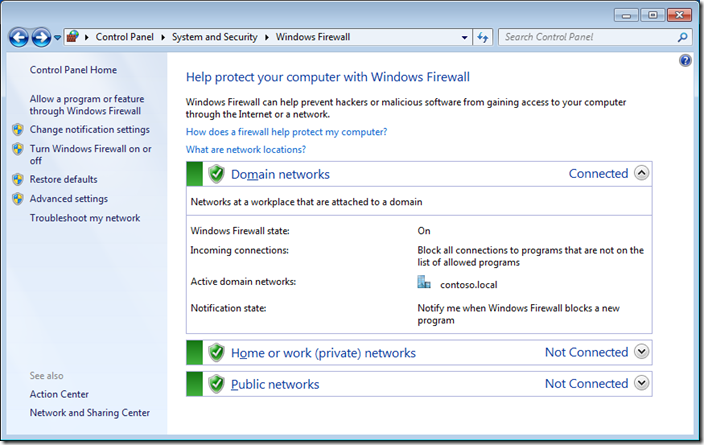
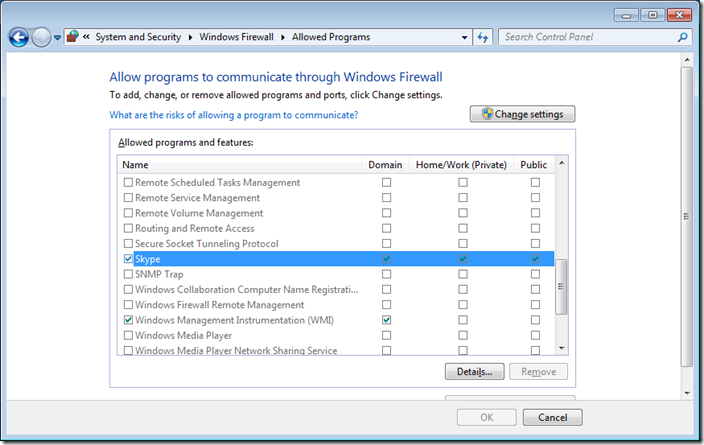
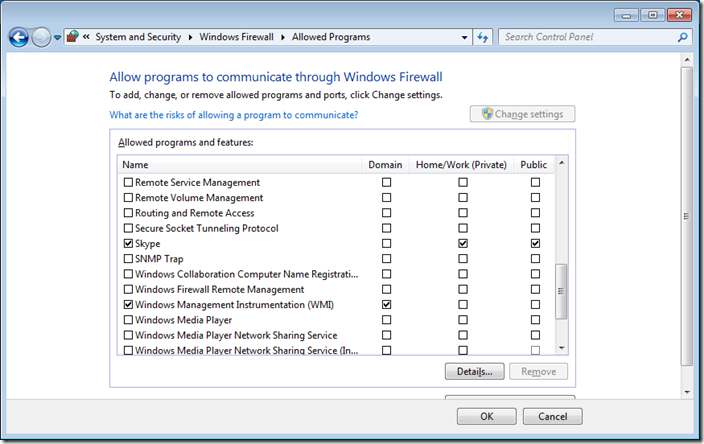
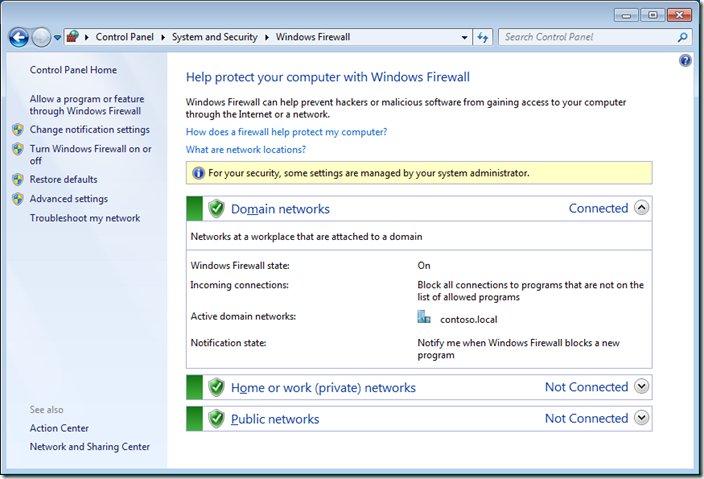
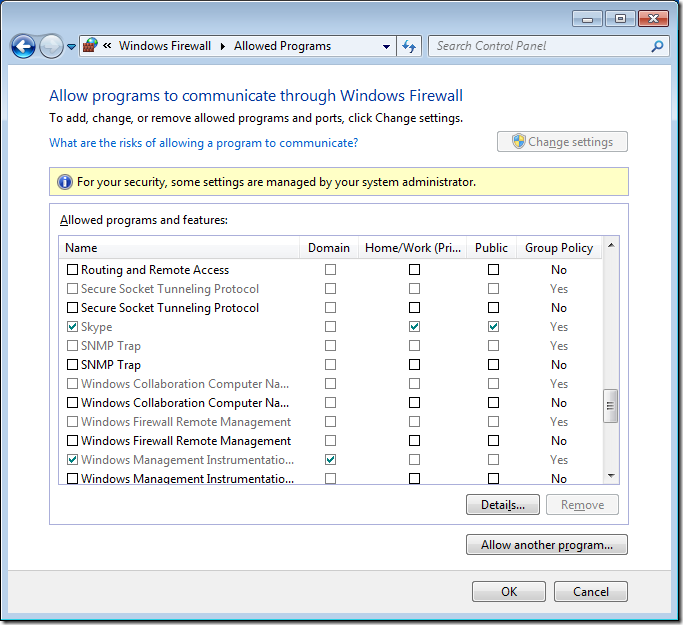
Step 3 optional. We are going to have a quick high level overview of the firewall rules by clicking on on “Allow a program or feature through Windows Firewall†in the left hand pane.
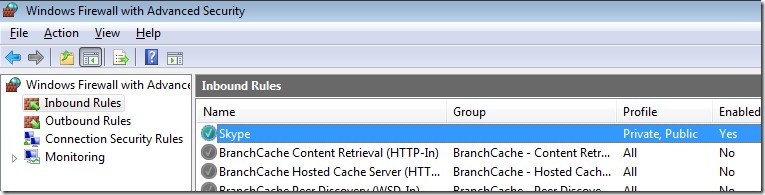
As you can see Skype has been setup to work in the Domain, Private and Public profiles. In this example we are going to configure this so that it will only work in the Home/Work and Public profiles so that users cannot use Skype when they are connected to the corporate domain via the LAN.
Note: that the options here are locked out as you have not yet elevated your credentials.
Step 4 optional. Click Cancel
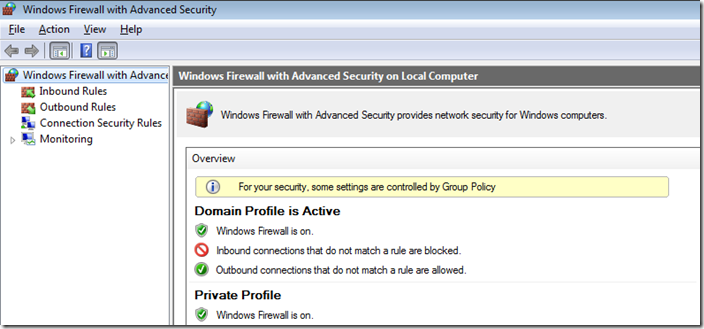
Step 5. Click on “Advanced Settings†on the left hand pane.
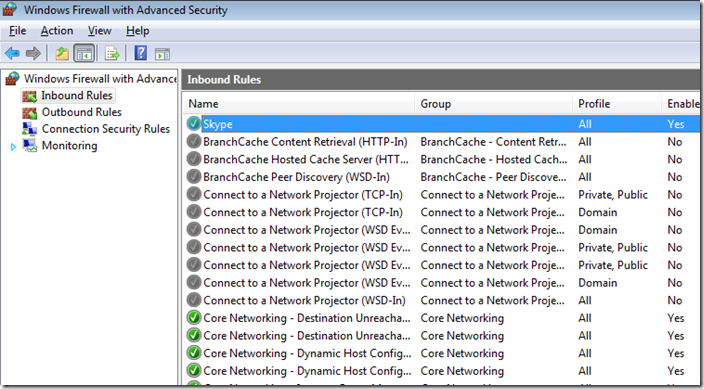
Step 6. Click on “Inbound Rules†and then double click on the “Skype†firewall rule entry on the right hand column.
Note: The currently configured Profile is set to “Allâ€
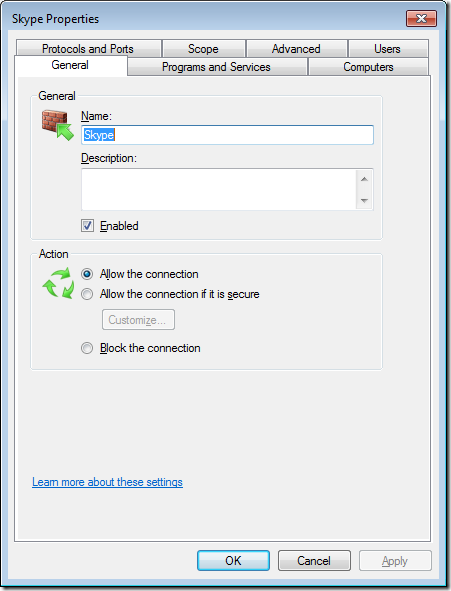
Now we will configure the Skype rule to be disable using the domain profile however you can also use this properties dialogue box to configured other granular setting. I recommend that you go though all these tabs and become familiar with all the setting you can control using this dialogue box.
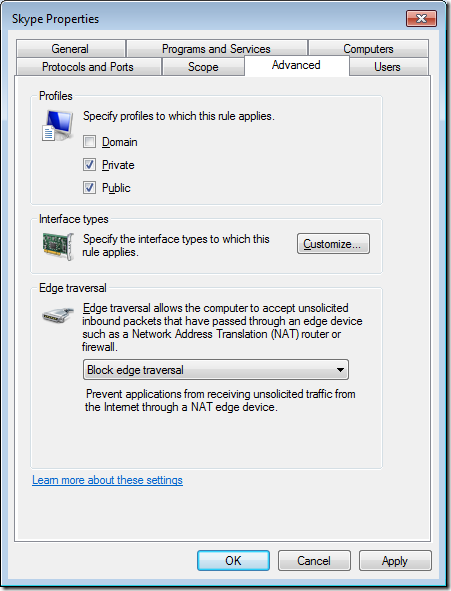
Step 7. Click on the “Advanced†tab
Step 8. Un-tick the “Domain†check box and then click “OKâ€
Note: The Profile is now configured to “Private, Publicâ€
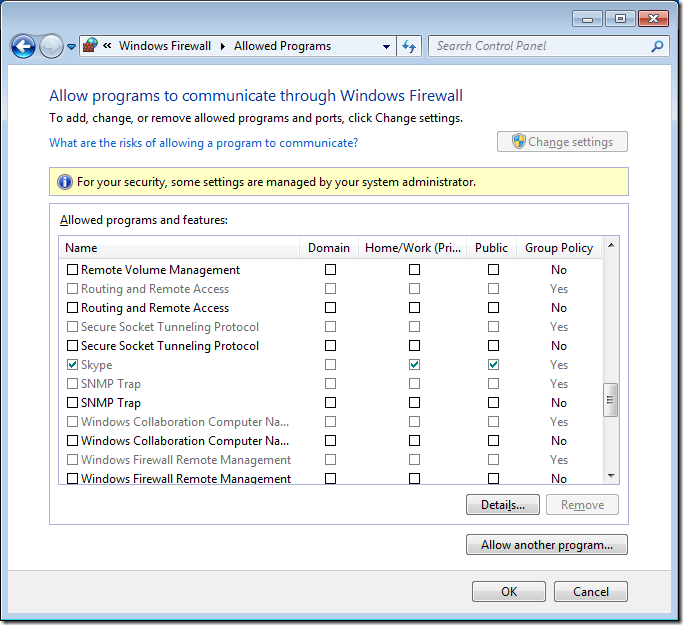
If you go back into the “Allow programs to communicate thought Windows Firewall†option you will now see that the Domain options for Skype has been un-ticked.
Now you need to test your firewall rule set to make sure that it behaves as you expect. Assuming everything is OK then you export your firewall rules so you can import them into a Group Policy. You may also want to save export the rule set before you begin to make sure you have something to role back to in case you totally stuff up the rule set and break your network.
Exporting Windows Firewall Rules
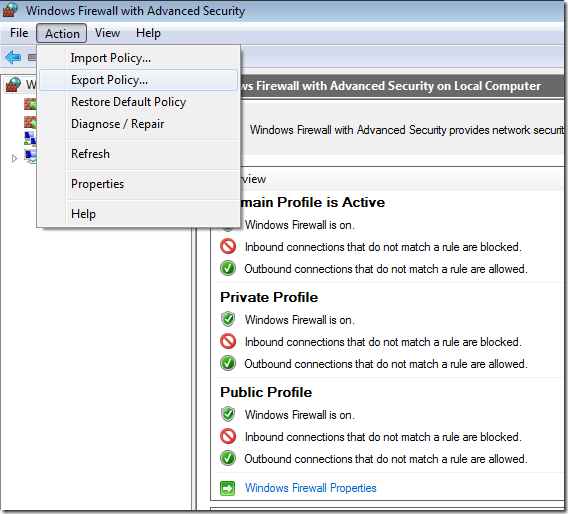
Step 1. In the Windows Firewall with Advance Security section click on “Action†in the menu and then “Export Policyâ€
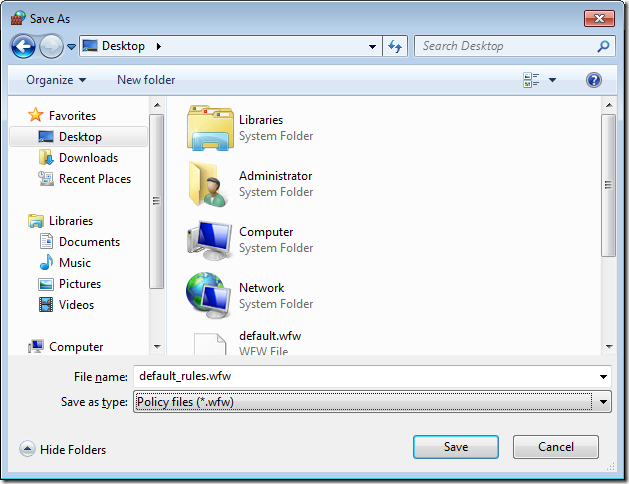
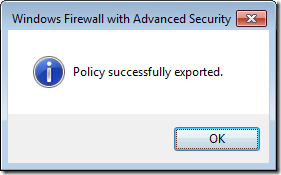
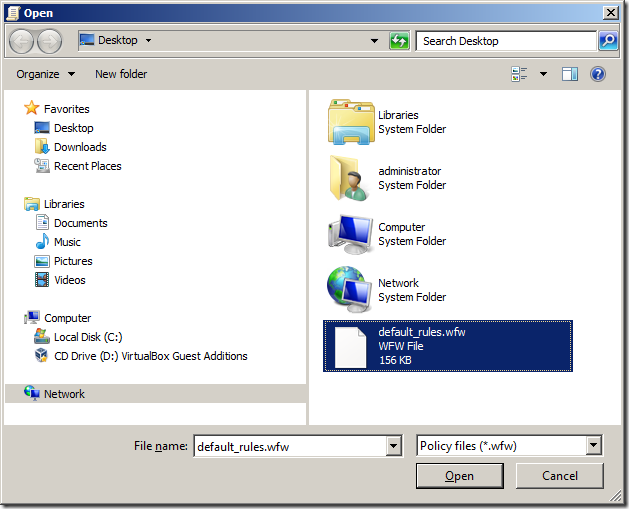
Step 2. Select a location to save your firewall rules and then type the name of the file you want to save them as (e.g. default_rules.wfw) then click “Saveâ€.
Note: If you have had to elevate as another user to modify the firewall rules then you will be saving the file in the administrator accounts profile.
Step 3. Click “OKâ€
Importing Windows Firewall Rules into a Group Policy
Now that you have exported the firewall rules we will now import the exported file into a group policy so that you can apply the same rule set to all the workstations on your network.
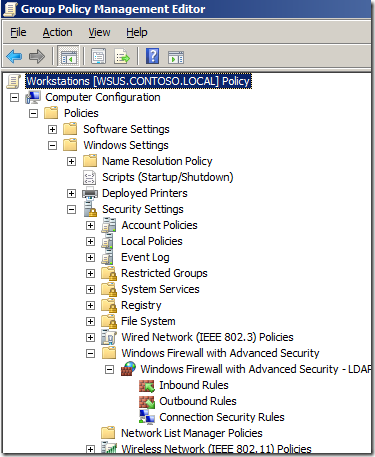
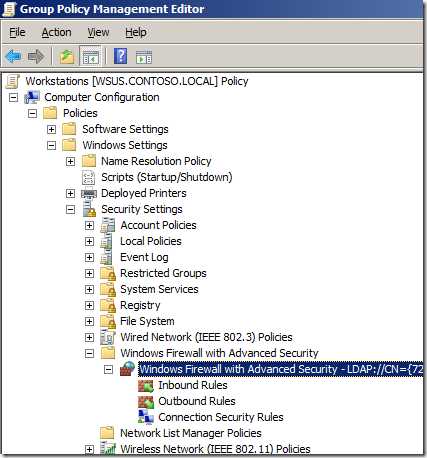
Step 1. Edit a Group Policy Object (GPO) that targets the computer that you want apply these firewall rules applied.
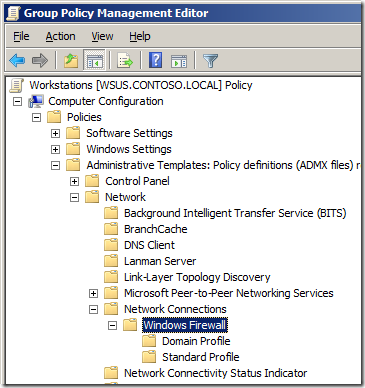
Step 2. Open Computer Configuration > Policies > Windows Settings > Security Settings > Windows Firewall with Advanced Security and click on “Windows Firewall with Advanced Securityâ€
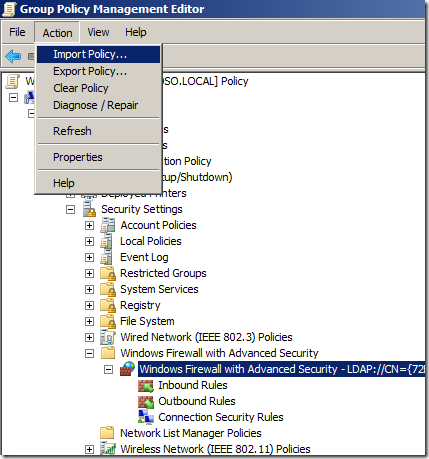
Step 3. In the menu click on “Action†and then “Import Policy…â€
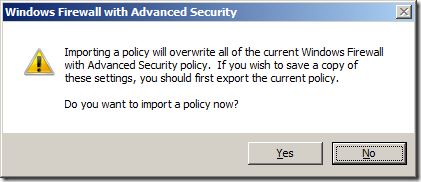
Step 4. Click “Yesâ€
Note: This is ok if you have not done this before however if this is the second time you have done this you might want to create a new GPO and import the rules into that one so as to not to blow away your existing policy rules.
Step 5. Select the firewall rule export file that created before and click “Openâ€
Wait…
Step 6. Click “OKâ€
Done.
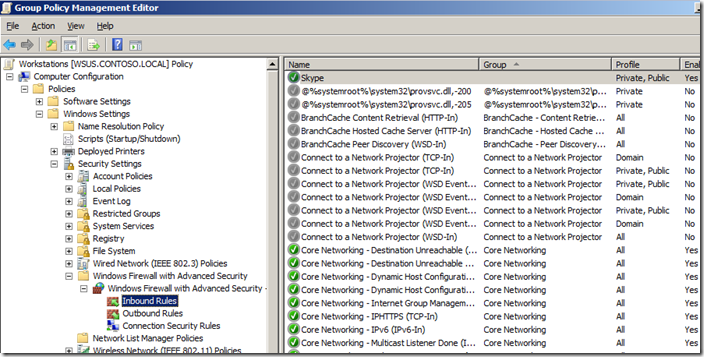
You can now review the rules that have been imported into the GPO.
Note: You can see how the Skype rule is configured as Private, Public as we configured before on the local computer. If you want to change the again you can simple double click on the rule and customise the rule how you want from within here.
You can also selectively disable rules and cut, copy & paste rules between separate GPO’s. This is how you would merge rules if you imported the rule set from into a new GPO back in step 4.
How to copy, delete or disable a rule… 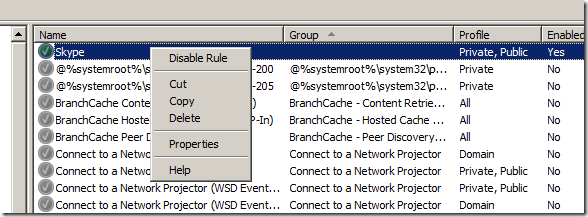
How to paste a rule into an existing policy… 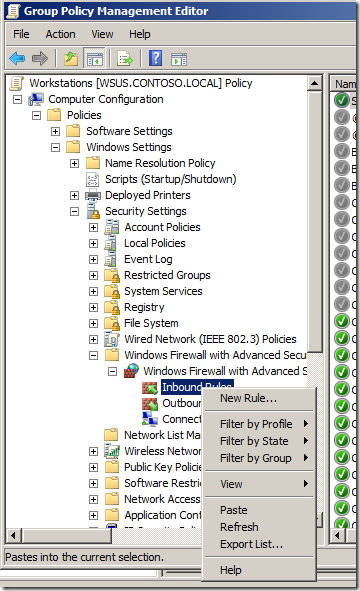
You should now be notified that in all the firewall dialogue boxes (see images below) on the workstation that the firewall policy is now being controlled via group policy.
Note the new column that states weather this is configured by Group Policy. Each rule is list twice as one represent the firewall rule controlled via Group Policy that cannot be configured and the other represent the local rule which can still be enabled by the local administrator.
How to exclusively apply Group Policy Firewall rules
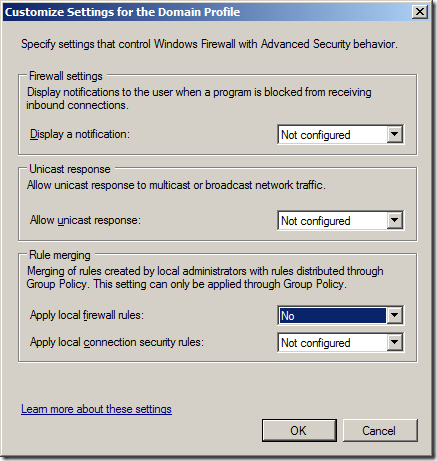
If you don’t want the local administrator to be able to apply additional firewall rules to the network then you can also configured it so that the Group Policy rules are exclusively applied to the local firewall.
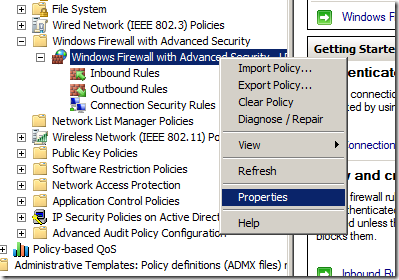
Step 1. Again open the same GPO that you have the firewall rules applied and navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Windows Firewall with Advanced Security and right click on “Windows Firewall with Advanced Security†and click “Propertiesâ€
Step 2. Click on the “Customize..†button in the Setting section
Step 3. Change the “Apply local firewall rules:†option to “No†and click OK
Now if you go back to the “Allowed Programs†under “Windows Firewall†you will notice that the Domain column is now totally greyed out and no rules can be applied to the domain profile even if you are a local admin.
Hopefully you this will have given enough to start controlling your windows firewall using group policy.
If you are feeling really adventurous you can also do the same thing to your servers to keep them secure as they are a lot more static with the firewall rule requirements which makes them even easier to manage. For example you could export the firewall rules of your SQL server and then import them into a GPO that is applied to all your other SQL Servers. This way when ever you move a computer object into the SQL Server OU the firewall rules are automatically setup and enforced… Nice..
![image[76] image[76]](https://www.grouppolicy.biz/wp-content/uploads/2010/07/image76_thumb.png)




Blog Post: How to manage Windows Firewall settings using Group Policy http://bit.ly/aZ4HaR
How to manage Windows Firewall settings using Group Policy http://j.mp/dD9CEM
How to manage Windows Firewall settings using Group Policy http://t.co/C0XY2FA via @alanburchill
When I try to export the inbound rules, my only options are txt or csv. The import process needs wfw extension. You do not mention this in your instructions. How did you export as wfw?
What can I do if the “allow a program or feature through Windows Firewall” line is greyed out on Windows 7 Enterprise and can not be clicked?
Sounds like you have a group policy applied that prevents the changeing of that setting… Or you are not a local administrator of your computer.
@alanburchill So to the internets – Best Practice: How to manage Windows Firewall settings using Group Policy: http://t.co/1dYEGoMi
ıf you want to block a program easily through windows firewall just use:
Firewall app blocker (Portable freeware)
http://www.sordum.com/?p=7633
@pnagaev политики на брандмауÑÑ€ раздаютÑÑ?
http://t.co/nWXelacx
http://t.co/24RDLJX4
Nice guide thanks allot.
Just one question, if you aply a GPO on domain level in my case a port block command, and its is replicated to a server , then fixed the gpo by turning it off again but the server still has it in affect and cant be deleted.
How to change it back
To block any app take a look at freeware tool Process Blocker http://www.processblocker.com
Well done sir!! However, …there are those who STILL do not know how to setup GPO’s for firewall. I wish I had months’…
heck, even years to do this but I don’t. I’d tried to do this like Microsoft said; but I don’t know if the setup I’ve done will work.
I need your input. No…I need your help. I do mean help. HELP!!
Start small… apply a policy to just one computer… then expand the scope until you are confident that it works
Nice posting. These tips are really tremendous to sale our home. I think it would be effective for all.Thank you for sharing with us. keep it up. Outsourced IT Services Dallas
Our IT consulting approach is service-oriented. We work with clients to find solutions to their needs rather than trying to fill billable hours or resell equipment. Our IT consultants work as efficiently with your IT budget as we do with our own. Our proficiency coupled with our high standards for quality and service provide our clients with outstanding value. As a result, every customer is our best reference.
http://www.lgnetworksinc.com/
Just wanted to say thanks, solid article even if there are a few too many spelling mistakes 🙂
I am looking for the commands to allow all TCP, UDP and ICMP traffic. Then make a firewall that does the same thing via GPO. Why? It stinks not being able to RDP to a machine or ping it and turning off the firewall causes other issues.
Hi Regular,
you can make use netstat on dc, if you are deploying DWFP by GPO.
Recently we deployed default windows firewall policy on all our prod win 7 system around ~1800 desktop,
from GPO, with great plan and change mgmt approvals. we successfully deployed,without affecting any existing AD environment leaving intact.
Regards
Raj
Basavaraj.R Navalgund
Great post, is there a way to set the Firewall GPO per user? I would like to set the FW rules on the terminal server depending on specific user.
Hi Tomas,
per user! yes,
Apply the FW policy with all requirements settings for one of the user ( on one of the desktop) and export that policy and import to users containing the OU and apply it, who require same template kind of firewall from GPO.
it may not be good idea to have each user having their own kind of firewall , if you are having 4-5 kinds of department who requires slightly different FW, you can go ahead and deploy it.
However you can always allow user to modify their local policy slightly.
Hope you find this useful.Thanks
Regards
Raj
Basavaraj.R Navalgund
thanks vnc can not default policy
thanks good morning http://ezgipleksi.com
buhuiuuty98ty7tyt
Firewall Settings can stop communication between a User’s computer and other computers?
Hi anonymous,
No, However it’s depends on how you are going to deploy firewall,
Regards
Raj Navalgund
Hi,
I need to do this in the LGPO area. I was wondering if you can do this from the cammand line. The wfw file doesn’t seem to work with the LGPO.exe for the import.
Thanks,
Todd
Healthcare research paper writing services are essential and it has become very popular for those seeking healthcare essay writing services since most of them seek Healthcare Assignment Writing Services.