Recently, I have been working a lot with PowerShell to automate the creation of a full AD site OU structure (with Group Policy and all) along with all the necessary delegated permissions. One of the limitation of the out of the box AD PowerShell commands is there is no easy way (but apparently there is a really hard way) to delegate permission to Active Directory OU’s. Luckily Quest Software have helped a lot here and they have offered a set of FREE PowerShell commands for Active Directory called “ActiveRoles Management Shell for Active Directory†one of which is called Add-QADPermission which greatly simplifies the process of delegation security in AD.
The Add-QADPermission command can be used to add an DACL security descriptor permission to any AD object with a distinguished name such as users, computer or OU’s. Therefore you can use this to delegate permission to OU similarly to running a “Delegation of Control Wizard†in Active Directory Users and Computers console (see image below).
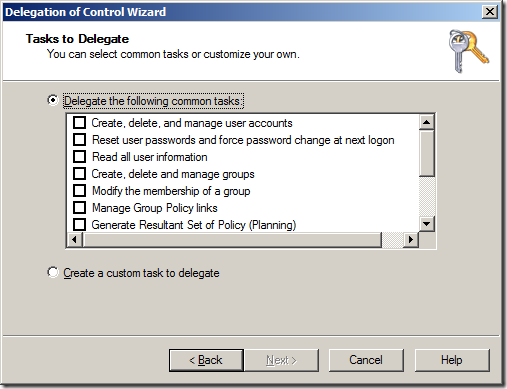
This wizard allows you to delegate some common tasks (see below) to your OU’s in you Active Directory however the permissions they apply are not straight forward simple permissions.
 |
 |
What I will show you how to do is how to perform some of the common delegation tasks that the “Delegation of Control Wizard†using a PowerShell command so you can automate the process for creating new OU’s in your environment. I know this is not strictly an Group Policy topic but it is one closely related and one I think many Group Policy admins will find useful.
The Command tasks I will show you are the one’s that I almost exclusively use when delegating permissions to Active Directory, they are:
- Create, delete and manage user accounts
- and Groups
- and Computers
- Reset user passwords and force password change at next logon
- Modify the membership of a group




Blog Post: How to delegate AD permission to Organisational Units using the PowerShell command Add-QADPermission http://bit.ly/dcXL9O
How to delegate AD permission to OUs using PowerShell. http://t.co/OGMAKjv via @grouppolicy_biz Good stuff that I might have to "borrow"
RT @alanburchill: Blog Post: How to delegate AD permission to Organisational Units using the PowerShell command Add-QADPermission http://bit.ly/dcXL9O
How to delegate AD permission to Organisational Units using the PowerShell command Add-QADPermission http://t.co/7RHgwWP
How to delegate AD permission to Organisational Units using the PowerShell command Add-QADPermission
Is your organization sensational? Is that why you spell it organisational?
You spell Organisation with an S in Australia…
Allan;
When I try to use the Add-QADPermission commandlet (following your example above) in a test environment I get the following error:
Add-QADPermission : The search filter is invalid.
At C:\WindowsPowerShell\test-it.ps1:33 char:18
+ Add-QADPermission <<<< -Identity "OU=New-OU,dc=XXX,dc=XXX=dc=XX,dc=XX" -Account "-XXXX Delegation of Authority\Security Role Groups\Role-Adm-Account-Management" -Rights GenericAll -ApplyTo ChildObjects -ApplyToType Group
+ CategoryInfo : NotSpecified: (:) [Add-QADPermission], LdapException
+ FullyQualifiedErrorId : System.DirectoryServices.Protocols.LdapException,Quest.ActiveRoles.ArsPowerShellSnapIn.Cmdlets.AddPermi
ssionCmdlet
I have tried both with and without the '-identity' parameter specified and with the input string as above and also in a variable.
I haven't run into any similar problems running other commandlets from the snapin but this one has me stumped. Any suggestions as to what I've got wrong.
Not sure if it is just how you typed it but… -Account “-XXXX Delegation of Authority\Security Role Groups\Role-Adm-Account-Management” appears to be wrong… there should not be more than one “\” in the group name…
Okay, now I get.
WARNING: Can’t lookup account for identity: ‘XXX.XXX.XX.XX\Role-Adm-Account-Management’
WARNING: No valid accounts specified. Searching permissions for all accounts.
WARNING: Can’t lookup object for identity: OU=New-OU,dc=XXX,dc=XXX=dc=XX,dc=XX
I’m running my testing at (this point) as Domain Admin in the test environment so why can’t I look up the identity?
Looks like you are not using a valid Netbios domain name… should only be 15 characters with no dots
Your post helped me a lot, but had some issues with delegating Reset Password Permission
Here is what I found out
The command: Add-QADPermission “OU=People,DC=Contoso,DC=Local†-Account “CONTOSO\User Operators†-ExtendedRight User-Change-Password -ApplyTo ChildObjects -ApplyToType User
need to be changed to
Add-QADPermission “OU=People,DC=Contoso,DC=Local†-Account “CONTOSO\User Operators†-ExtendedRight User-Force-Change-Password -ApplyTo ChildObjects -ApplyToType User
User-Change-Password
Permits changing password on user account.
User-Force-Change-Password
Permits reseting password on user account.
Reference: http://technet.microsoft.com/en-us/library/ff405676.aspx
If you use the delegation Wizard to delegate the Reset Password permission, you’ll find out the a get-qadpermission, returns RIGHTS: Reset Password, not Change Password
Hi to all, it’s in fact a pleasant for me
to go to see this site, it consists of valuable Information.
My homepage; pdf books
I can’t see a way to delegate control to an OR, i can easily do it for group.
These powershell extensions appear to no longer free since the company changed to One-Identity.
Instead its a 30 day trial.