Isolate your Administrator Resources
If you are an organisation of any significant size you probably have a delegated cretin duties to specific teams (e.g. help desk or desktop support) via the way of administrator groups. This would allow you to easily grant the required permission for a IT support person to a specific user by only adding them to one group. However one of the permissions that is normally delegated is the ability to change group membership.
If all the groups in your organisation were in one location then a person who simply has the ability to add and remove member from group could in theory given them self more administrator access by adding them self to a higher level administrators group. To prevent this from happening you should segment all administrator or higher level permission group in the AD structure so that only the most trusted administrators can make changes to these admin groups.
Also remember there is a difference from having administrator or delegated access to the Active Directory object and local administrator access to a computer. Therefore under each Workstations and Servers resources OU you may also want to consider creating an Administrators OU that contains the local administrator security group of the computers accounts in the top level OU’s. This would also assist and being able to easily delegate administrator access to both the computers AD object but also local administration as they are all contained in the one location in AD.
Another reason to you have a dedicated Administrators OU at the top level is so that your administrator accounts are not subject to the same SOE Group Policy setting than the rest of your users. Administrator accounts should also be a separate accounts for IT administrators as their normal day to day accounts should be subject to the same configuration as the rest of the staff. While this is something that a lot of IT staff loath I think it is very good idea for IT staff to set the example as to how computers are configured and dogfood their own configuration. Ensuring that IT staff also have a separate administrator account also reduces greatly reduces the security risk associated with doing day to day operations (checking email, surfing web) with administrator permissions (see How to use Group Policy to make Windows 7 90% more secure).
For more information on assigning local administrator access to computers via group policy check out my other article How to use Group Policy Preferences to Secure Local Administrator Groups
| Isolated Administrator OU Structure |
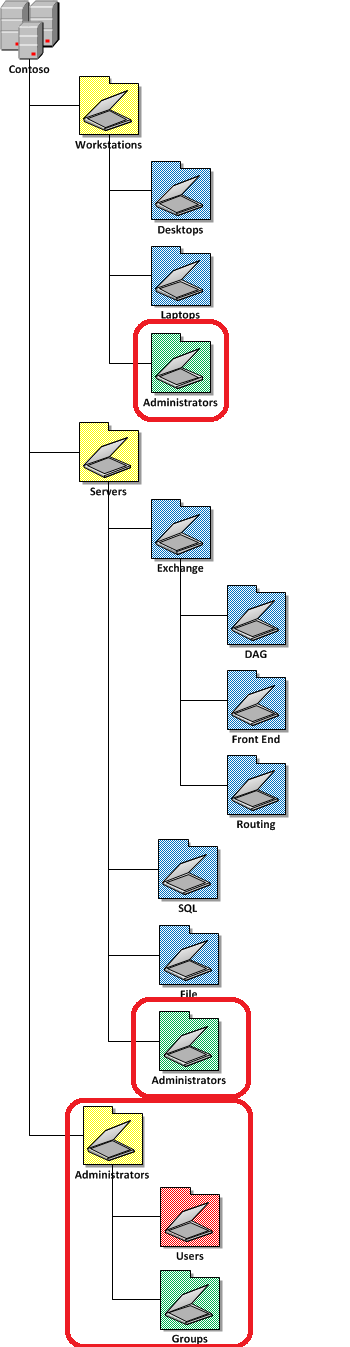 |
Reference
TechNet: Using Security Filtering to Apply GPOs to Selected Groups
Create a separate OU for administrators and keep this OU out of the hierarchy to which you apply most of your management. In this way administrators do not receive most of the settings that that you provide for managed users.
Have administrators use separate administrative accounts for use only when they perform administrative tasks. When not performing administrative tasks, they would still be managed.
Do you REALLY need more than 4 levels?
Below is an example of a combined Organisational / Location / Resources / Sub Resource model that you could consider for 4 level deep this structure or a variation of these levels should pretty much handle most any requirements of any organisation. As you can see from my examples below you would be fairly pushed to require an OU structure more than 4 level deep so ask yourself this question if you start to contemplate a 5+ level structure.
| 4 Level OU Structure |
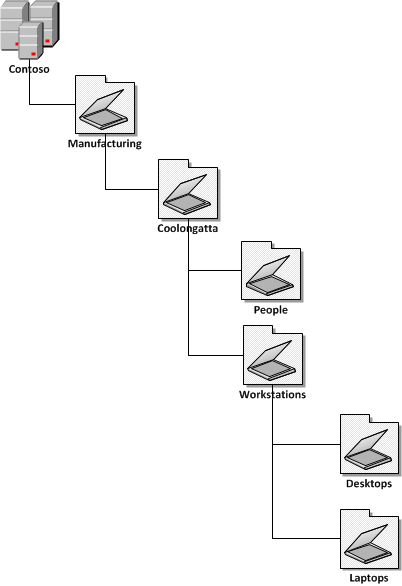 |
I am so confused… how about you just tell me what OU structure to use?
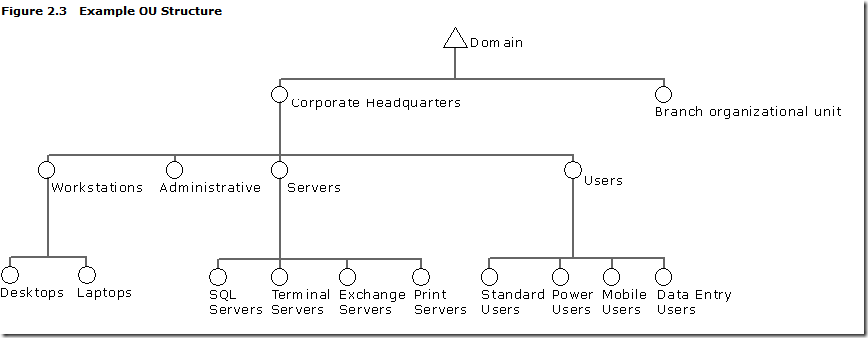
Ok. So your brain is probably about to explode with all the different OU types and you just don’t know where to start. Well in the TechNet article Designing an OU Structure that Supports Group Policy we see a really good OU structure in Figure 2.3 Example OU Structure (see image below). You should be able to see how this is an three level OU structure combining Location/Resource/Sub-Recourse and that the naming convention of the structure match closely with guidelines we discussed above. You may find that this example will fit all your needs exactly or you may end up customising the design over time but either way this is a pretty good design that I have seen work in may organisations.
I hope the above AD design ideas have helped you design your organisations OU structure. Certainly there is no one size fits all model and you need to carefully consider your requirements before committing to a design.
Now I recommend that you you should visit the second part in this series where I list my Group Policy design rules which heavily depend upon. This should hopefully show you how designing a good OU structure can help you substantially make administering Group Policy (and your entire AD) a lot more easier.
Other References
- TechNet: Designing an OU Structure that Supports Group Policy
- Designing an OU Structure that Supports Group Policy
NEXT > Best Practice: Group Policy Design Guidelines – Part 2





Blog Post: Best Practice: Active Directory Structure Guidelines – Part 1 http://bit.ly/bVkygi
Blog Post: Best Practice: Active Directory Structure Guidelines – Part 1 http://bit.ly/bVkygi
Best Practice: Active Directory Structure Guidelines –Part 1 http://bit.ly/cICPDp
RT @xenappblog: Best Practice: Active Directory Structure Guidelines –Part 1 http://bit.ly/cICPDp
RT @xenappblog: Best Practice: Active Directory Structure Guidelines –Part 1 http://bit.ly/cICPDp
OdliÄno Å¡tivo za sve koji su odgovorni za strukturu AD-a! http://fb.me/zUZU5U5w
@Froosh u mean? https://www.grouppolicy.biz/2010/07/best-practice-active-directory-structure-guidelines-part-1/
. @Mixailovich Err, doh, yes that one too 😉 http://bit.ly/cJApsO
Best Practice: Active Directory Structure Guidelines – Part 1 http://bit.ly/9oDQJq
Hi Alan, great article – nice clean overview of this difficult subject.
One question about the different graphic files you created, for example this one: https://www.grouppolicy.biz/wp-content/uploads/2010/07/image_thumb78.png
How did you create it – Visio?
And how did you get the graphic elements used..
Need it to document our network-layout at work.
-Jonas, Denmark
Its 100% Visio 2010…
@thommck There are some great ideas about Active Directory structure (OUs) in this series from @alanburchill. http://bit.ly/ebQlLS
Best Practice: Active Directory Structure Guidelines – Part 1 http://t.co/5A6ak0V via @alanburchill
Good Article
I wanted to include some informtaion about the naming of OUs where it says :”When naming your Organisational Unit make sure the name you are using are short and to the point…” There may be technical limitations that may affect long names.
During binds to the directory, simple LDAP bind operations limit the distinguished name (also known as DN) of the user to 255 total characters. If you attempt a simple LDAP bind with more than 255 characters, you might experience authentication errors
Active Directory Maximum Limits – Scalability
http://technet.microsoft.com/en-us/library/active-directory-maximum-limits-scalability(WS.10).aspx
Best Practice: Active Directory Structure Guidelines – Part 1 http://t.co/3OBagYfF via @alanburchill
Best Practice: Active Directory Structure Guidelines – Part 1 http://t.co/LDCB4xuI via @alanburchill . useful as I am restructuring our AD.
Best Practice: Active Directory Structure Guidelines
http://t.co/BNi4AcIO
Best Practices al diseñar o reorganizar AD http://t.co/MuCB4uLB
Best Practice: Active Directory Structure Guidelines – Part 1: http://t.co/wVwTezBr
Best Practice: Active Directory Structure Guidelines – Part 1: http://t.co/nTIzr8gs
Thank you this is very much appreciated. I am working on a deployment for a organization with 4 distinct locations that includes a marriage to Apple OpenDirectory as well as FreeBSD OpenLDAP. Having a well thought out explanation like this is fantastic. It has helped me explain the complexities of designing the right solution to all members of the team. I still have not drafted the final plan but it is giving some great ideas so hopefully I can achieve this shortly.
Cheers,
Mikel King
Apple Open Directory?? Don’t go there, it’s a trap! 😉 Recommend to use AD + extend schema to support OS X
I’m new to Active Directory and this is very usefull.
I have a question about the Resource Structure Example image sample above .
I know that it is only an example but :
the Groups OU contains Roles and Resources groups.
What they means?
Does Roles contains groups like Officers, Employees, etc?
Thank you very much.
Hi,
i have configured one domain. i want configure some
group policy by organzation units. i have created ou.and i move some user in that ou. but i dont know how to
link this ou with group policy i did try many times but i did not sucess any one help me…
“you probably have a delegated cretin duties to specific teams”
WTF?
Best Practice: Active Directory Structure Guidelines; Part 1: http://t.co/Lzspv4Kt
Best Practice: Active Directory Structure Guidelines – Part 1: http://t.co/dp4nSVFdUw
Very Nice tanQ grouppolicy http://chatflash.ir/
Very nicely explained. Thank you good sir.