
One problem I see all the time is IT administrator never being able to control who is a local administrator of any particular computer. The problem is that when you give someone local admin access to a computer (because they legitimately need it) you cant stop them from giving admin access to someone else on the same computer. When this does happen it is also its almost impossible to discover as you have to run a query every computer to see who is in the local admin group and then figure out which account should be a member. Once solution to this is of course following Microsoft best practice and not give your users local admin access to their PC or Server and in an utopian environment this would be possible but we all live in the real world where managers have admin access to their PC’s and developers are allowed to install any software they want. So how do you give a users full admin access to a computer but stop them from adding more people to the local admin group on a computer? Use Group Policy Preference of course.
But first a bit of History… Since Group Polices were first introduced with Windows 2000 there was an setting called “Restricted Groups†which allows you to control the membership of a group. This option had two modes one called “Members†option which I also call the “Iron Fist†mode and the other “Members Of†option which is much gentler. The “Members†option removes any groups or users that are not explicitly specified and the “Members Of†option just adds a specific group which out removing any existing groups. The “Members†option was really good at cleaning up those rogue members of the local admin group but its was also really hard to setup as you had to have a new group policy every time you wanted a different list of members in local group on a computer. The “Members Of†option was a lot easier to maintain as you could layer multiple group policies on top of each other but this normally resulted in just adding another layer of group to the pile of groups that were already in the local administrators group. The other problem was the “Members†option would override the “Members Of†option so there was really no way of mixing the two modes.
BUT… Group Policy Preferences can use Variables which enabled you to be very extremely granular in controlling you local admin group while still having “Iron Fist†control. Muuhhaaaahahahahah!!!
How do I setup a restricted local administrator group?
The following steps will need to be applied to a GPO that is applied to the computer objects you want to control the local administrator groups. Note: You must make sure you don’t have any other Group Policy “Restricted Groups†settings applied to your computers as they will always override the group policy preferences settings.
Step 1. Open the Group Policy Management Consol and edit the group policy that is applied to the scope of computers that you want to control.
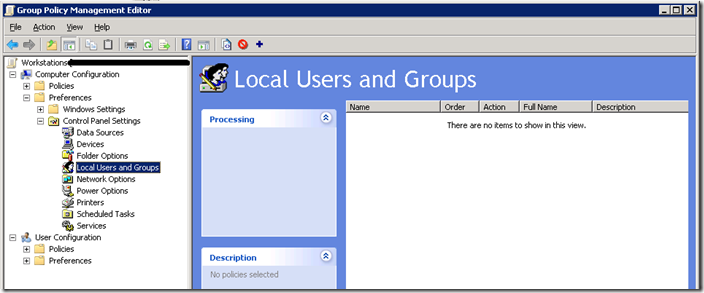
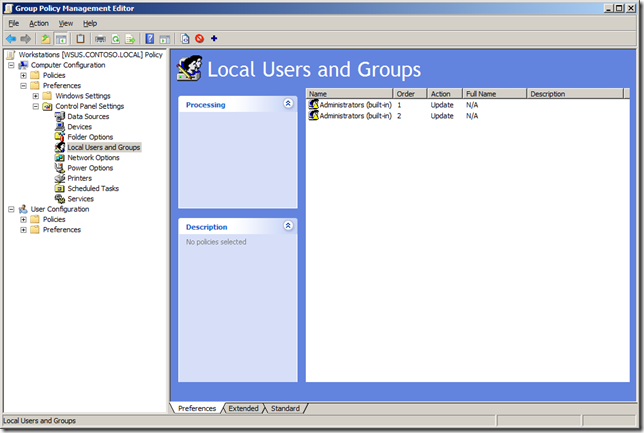
Step 2. Go to the Computer Configuration > Preferences > Control Panel Settings > Local User and Groups option (see Image 1.).
Image 1. Local User and Group
Step 3. Now click on Actions > New > Local Group
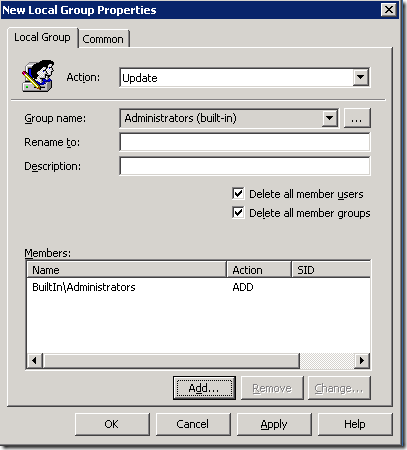
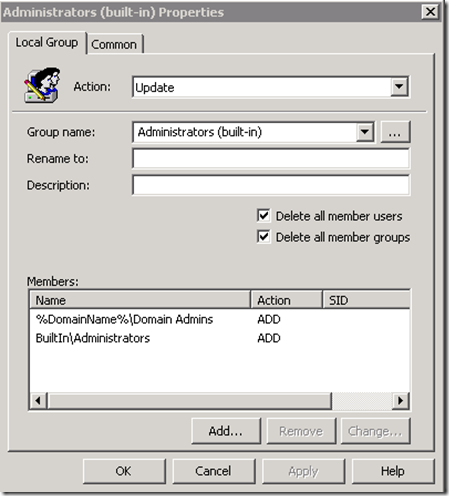
Step 4. Now you will be need to select “Administrators (built-in)†from the group name as this always selects the built-in administrators group even if you have renamed it to obfuscate the name of the admin account.
Step 5. Tick both “Delete all member users†and “Delete all member groupsâ€. These two options will automatically remove any users or groups that are not explicitly being added to the group. You only need to do this on item number 1 in the list of settings as that setting will be processed last.
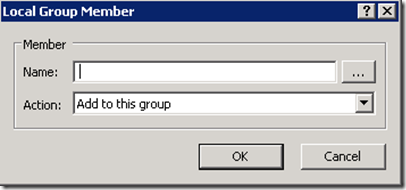
Step 6. Now you will need to make sure you have added back in the Domain Admin’s and Local Administrator groups so that you don’t totally lock yourself out of the computer. To do this click the “Add…†button to bring up the “Local Group Member†dialogue box (see Image 2)
Image 2. Local Group Member
Step 7. Now type “BuiltIn\Administrator†in the Name field and click OK (see Image 3.)
Note: The image below is wrong… it should be “BUILTIN\Administrator”
Image 3. Local Administrators group added to the local administrators group
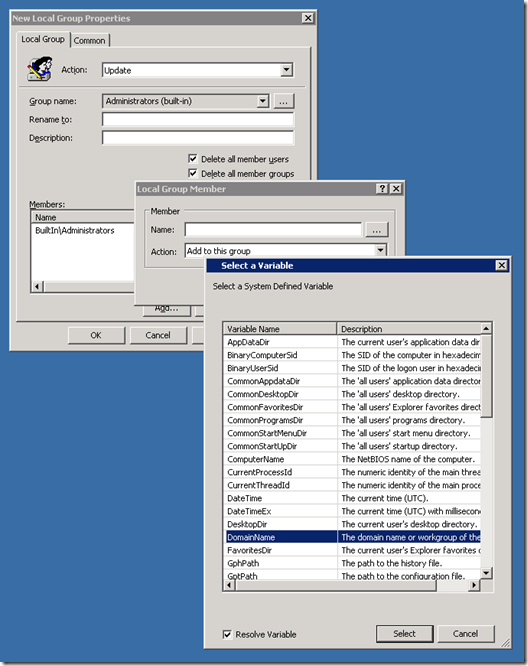
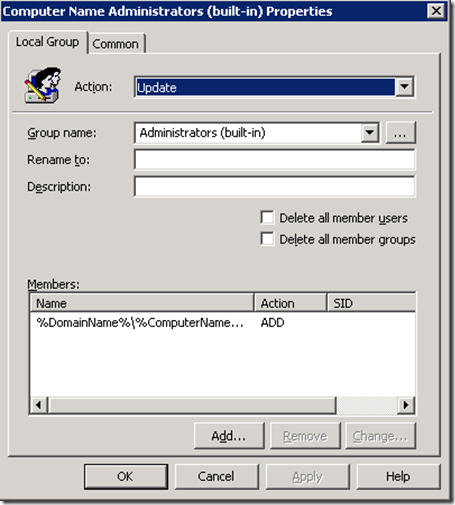
Step 8. You should also add “DOMAINNAME\Domain Admins†as it is a good practice to have the DA account as a member of the local admin group on all computers in the domain. To do this we are going to use the DomainName variables. Click “Add…†again and now click in the “Name:†text field and then press F3. This will now bring up the “Select Variable†dialogue box (See Image 4.). Click on the “DomainName†field and press “Select†and then “OKâ€. (alternatively you could type %DomainName% in the name field and just press OK.)
Note: The image below is also wrong… The bottom image should be “BUILTIN\Administrator”
Image 4. Selecting the DomainName Variable
You should now see the following which will restrict the local administrator group to only have the Domain Admins and the local administrator.
Note: The image below is wrong. It should be “BUILTIN\Administrator”
Image 5. Basic local administration group setting
So what you as? I can do this already with the “Restricted Groups†Group Policy setting. Well only having the local Administrator and Domain Admin’s in the local admin group isnot not much use unless you are willing to give everyone the local admin password or give them all Domain Admin’s privileges (Like that ever happens) when ever they needed admin access. Well again this is where Group Policy Preferences can help.
How to add individuals to a single computer?
Now we are going to go thorough how to add a uniquely named domain group to the local administrators group without having to set up multiple group policies objects. This scenario is very helpful if you want to grant a single user or group local administrators access on computer but still ensure that no other users or groups can be added without explicitly being approved. In the steps below the computer name is DESKTOP01 and the domain name is CONTOSO, we want to add the group “CONTOSO\DESKTOP01 Administrators†to the local administrator group but we also want the same to happen on DESKTOP02, DESKTOP03 and so on, each with their own uniquely named group based on the computer name.
Update: Having a unique group for each computer allows you to easily grant permission to for a single users to a single computer as there is a one to one mapping of domain groups to local administrator groups.
Step 9. Now go back and repeat steps 3 to 6 until you get to the Local Group Member dialogue box again (see Image 6.).
Note: This creates a second local administrator group entry in the list to work around an issue.
Image 6. Add Local Group Member
Step 10. Type “%DomainName%\%ComputerName% Administrators†in the Name text field and click “OK†(Image 7.)
Image 7. Configuration to automatically unique group to local administrators group
Now this will now automatically add a domain group called “DOMAINNAME\COMPUTERNAME Administrators†to the local administrators group on the computer to which the policy is applied and your group policy should look like Image 8.
Image 8. Two local administrator group settings
Update: There are two separate local administrator group setting in the policy, the first one is the setting you see in image 5 and second one is the setting you can see in image 7.
However the “CONTOSO\DESKTOP01 Administrators” group will only be added to the local administrators group on the computer DESKTOP01 if that group is already exists. Therefore you do not need to create the group until the need arises to add an individual user or group to just a single computer.
Update: This policy will not create the group in your Active Directory called “DOMAINNAME\COMPUTERNAME Administrators†and you don’t have to create it unless you want to use it to grant permission to the computer. Once you have created the group you can then add a single user to the domain group… or multiple user accounts and groups. The other advantage of having this domain group is that it is the only place where you can grant admin access to the computer without it being automatically removed there fore it makes auditing who is a local administrator on a workstation much easier as you only have to audit the domain groups. This means that you can even report on who has access to the computer when the computer isn’t even connected to the domain.
This group policy setting combined with the other setting made earlier (see Image 5.) will mean that the local administrator group on the computer DESKTOP01Â in the CONTOSO domain will have the following members automatically added to the group:
- CONTOSO\Domain Admins
- DESKTOP01\Administrator
- CONTOSO\DESKTOP01 Administrators
But ANY other users or groups will be automatically removed after the next group policy refresh. This does mean there is a slight window of opportunity for someone to slip in an un-authorised account into the local administrators group but they will get removed at the next policy update.
Side Note: I have found that users almost never complain that they cant add un-authorised user to the local admin account on computer. Go figure… 🙂
AWSOME!!!! I hear you say… but wait there is more…
How do I add additional broader groups to the local administrators group?
Now that you are able to granuarlly add a single user or group to the local administrators group on a computer you might run into problems id you have more than a 1000 computers due to AD Token Bloat Issues . So to get around this we can setup some more broadly applied administrator groups to the computer that will give admin access to only a subset of computers such as all workstations or only the SQL Servers in your organisation.
Workstations Admin Groups
To apply a Workstation administrators group to the local administrators group on all workstations make sure you have a group policy only targeted to your workstations. This is normally pretty easy as most companies isolate their workstations computer accounts to one (or a select) number of Organisational Unit.
Step 11. Go back and repeat steps 6 and 7 but this time add the group “%DomainName%â€\Workstations Administrators†in the name field. This will added the additional group “CONTOSO\Workstation Administrators†to the local admin group on all the workstations in your domain which will allow you to easily add all the Desktop Administrators in your organisation access to all the workstations without having to give them the local admin password or domain admin’s privileges.
Server Role Admin Groups
It gets a little tricker when you want to grant access to a server based on its role as server are sometime configured for multiple roles. So in these steps we are going to automatically added a domain group called “CONTOSO\SQL Server Administrators†to all the servers you have that have SQL Server installed on them. This will be very handy to making sure SQL service accounts or database administrators have admin access to all the servers that have Microsoft SQL Server installed. You can however make multiple version of these admin group for other roles (e.g. Exchange,SCCM,ISA) you just need to know what the best way to target the setting.
Step 12. First make sure you are editing a group policy that is applied to all your servers in your organisation.
Step 13. Repeat Step 9 and 10 and then we open the properties of the new policy setting and specify the group but this time we type “%DomainName%\SQL Server Administrators†in the name field.
Step 14. Click on the “Common†tab and then tick “Item Level Targeting†and click the “Targeting…†button.
Step 15. Click on the “New Item†in the menu bar and select the option you want to use to target all the SQL servers in your organisation and select the “File Match†option to look in the Program Files folder and see if a sub-folder exists called “Microsoft SQL Servers†(See Image 8). This is normally true for any server that has Microsoft SQL Server installed and so it will then automatically apply the SQL Server Admin group to that server if it was installed.
Note: In this example we tested that the “Microsoft SQL Server†folder exists but we could also make rule to test for the existence of a particular file or registry key.
Image 8. Testing to see if Microsoft SQL Server is installed.
Now any computer that SQL Server, MSDE or SQL Express installed will get the group “CONTOSO\SQL Server Administrators†automatically added to the local admin group.
This nice thing about this is that if SQL is installed on the server at some point in the future the SQL Admin group will be added automatically at the next group policy refresh without you having to do a thing.
Finally.. now you have tight control of the local administrator groups on all the computers in your domain it is now important to monitor and secure the domain groups that are being added to the local administrator groups as they now control who has admin access to all your computers. But I will save how to do that for another blog post…





Blog Post: How to use Group Policy Preferences to Secure Local Administrator Groups http://bit.ly/4MhTkO
How to use Group Policy Preferences to Secure Local Administrator Groups http://bit.ly/5DPmlu
A good write up when used in conjunction with auditing – How to use #Group #Policy Pref's to Secure Local Admin Groups – http://is.gd/6NWI7
This is where you lose me: “How to add individuals to a single computer?” Is this a required step to get all this to work? Also in the paragraph you do not list where this new group is going to be created. Im assuming it’s at the same location as the first preference was created? Also in that same paragraph, why would you want a different group for each computer (you said Desktop01, Desktop02, and Desktop03)? So you’re saying to create 3 groups (DESKTOP01 Administrators, etc)? Create these groups in the preferences or create the groups in Active Directory Users and Computers?
I just want a central group called WksAdmins, that I can add users to it and they will have the local admin access. Is that possible?
Very good article, I just got confused from this point on. Thanks…
I have made a few updates to this article and i have added another screen shot that should clarify how this should look like configured… Thanks for the feedback always appreciated.
See how to use Group Policy Preferences to Secure Local Administrator Groups http://bit.ly/5DPmlu
Alan,
Great post and thankyou. Been a fan of your work since TechEd09 and your performance with @superlilia!!
Question – We have approx 3000 machines on our network, and have a requirement for approx 500 users to have local admin rights on their machine. This solution looked perfect until you started takling about Token bloat issues, of which I am not familiar.
We don’t want to provide these users with access to all other 499 machines, and so the option to create a workstation-admins group won’t work for us. What are the implications of “Token Bloat” and do you have any suggestions how we can allocate an individual user local Admin rights to their machine only via GP or GPP?
Thanks in advance,
Mick
Never mind – I gave it some more thought, and created a sub OU that contained only the computers we wanted this to apply to and moved those machines that werw affeted by this into that sub OU. We the applied a new GP to only that sub OU with the “%computername% Administrators” being applied to it, and ensured that GP inheritnace to that OU is turned on. That way we’re not created a lot of unnecessary traffic etc and thus ensuring that we don’t get hit by “Token Bloat” issues … whatever they are!!! . Thanks again for you post on getting me started.
Mick
Token bloat is an issue when a user becomes a member of to many security groups… there is a limit of 500 to 1000 groups a user can be a member off (directly or indirectly) and then things will start to randomly break… this normally presents as an access denied or Out of Memory issue…. This may become an issue if you add one user to each of the 3000 security groups to give them admin access to all the comptuers… So… use %computername% administrators sparingly…
However if you are just creating the 3000 security groups and users are only going to be granted access to one of thoes comptuers then this is fine…
If you want to grant a single user (such as IT Support) admin access to all the workstations for this seperate OU then you want to apply another group called “Workstatation Administrators” which will be the same group applied to all the computers… that way a user can have admin access for all workstation by only being made a member of one group…
Hope it helps… Hope to see you at TechEd this year…
Hi,
This looks really useful but I’ve had no success at all in getting this to work in either our test lab or live network. The new members are not being added to the local group, but I can’t find any errors to say why. Is there any dependency on DCs for this functionality (ours are still Windows 2003)? Do you have any suggestions on how I can troubleshoot this?
Thanks
Robin
Hi,
sorry if my question will appear a bit stupid … I’m studing system servers by myself at home: enviroment test : Vmware with a W2k3 R2 domain.
Question: The screenshot above are of GPMC of windows 2008?? When I open my editor of policy there are different options. :((
Thanks for the furure answer.
Roberto
Yes… GPMC on Windows XP or Server 2003 would look different as they do not support Group Policy Preferences… GPMC on Vista/7 & 2008/2008 R2 would look the same (or very similar).
You version of AD should be fine…
Things to check…
1. Do you have the client side extentions installed
2. Have you split the “%computername% administrator” preference item into a seperate setting?
3. Have you done a group policy results report agains the computer to see what is being applied?
Your second point was spot on. I’d not followed your guide carefully enough and had added everything into the one preference item!
Thanks for your help
Robin
P.S. I don’t suppose you can use wildcard characters when identifying the new group member?
Robin. Yes.. You can use wild cards…
Is there an easy way to hide the Local Users and Groups control panel item from appearing?
Thank you,
John
You should be able to block the comptuer management contol pannel icon via group policy…. Under User Configuration > Policies > Administrative Templates > Control Panel > Hide specifiec Control Panel Items
Hi,
Great article. Is there a reason why you specify the domain name as a variable (%DOMAINNAME%\Domain Admins) as oppossed to the actual domain name (mydomain\Domain Admins)?
If you export the setting and apply it to anohter domain then the static “MyDomainName” will be wrong… This could be usefull in a single multi domain environment.
I am testing this GPO and whenever I add the BuiltIn\Administrators group to the GPO as in step 7 and test with gpupdate I get an error on the client: –
The computer ‘Administrators (built-in)’ preference item in the ‘Test Policy {8ACC7AF3-11F6-4F06-9586-45E 42F3C656}’ Group Policy Object did not apply because it failed with error code ‘0x8007056c A new member could not be added to a local group because the member has the wrong account type.’ This error was supporessed.
Have you seen this warning and why does it occur?
What is the exact text of the user or group you are trying to add to the BuiltIn\Administrators group?
How to use Group Policy Preferences to Secure Local Administrator Groups http://t.co/CNPznXl #mvpbuzz
I get a similar error to the one that IanG mentioned. I am confused as to why you would have to add the built in admin group to itself anyway. Were you trying to add the built in admin account? From my testing the built in admin account remained in my local admin group despite not being mentioned in the GPO.
Anyone know if it is possible to use a varible substring? ie. %ComputerName:~0,10% in Group Policy Preferences?
No … variable substrings are part of the CMD shell, and are only acted upon from within a CMD shell (.bat/.cmd Files run within the CMD shell).
When you pass %ComputerName:~0,10% as a parameter outside of a CMD shell, it passes as the string (w/out quotes): “%ComputerName:~0,10%”
Whereas passing %ComputerName% as a parameter outside of a CMD shell will pass the actual computername.
I’m having the issue as IanG. I’am adding a single userto a single server. (domain\username). Everytime the GPO’s update this error shows up.
Found the cause…
Instead of adding the single user to the single server, I added a second GPP adding an SG, single user in the SG. And used the above example for for adding an SG with the condition (common) of “file folder”.
Also, from MS http://support.microsoft.com/kb/842217 relates the the specific error
@MikeFi I would have tried creating a seperate Group Policy Preferece Item to add the seperate user…
I’ve tried various combinations and I can’t get your example to work at all. All I get is an Administrators group with Administrator in it and nothing else. The following error keeps showing up.
The computer ‘Administrators (built-in)’ preference item in the ‘testAdminGroup {1EC221BF-3E61-434D-817C-1C07EDA42FB1}’ Group Policy object did not apply because it failed with error code ‘0x80070534 No mapping between account names and security IDs was done.’ This error was suppressed.
I’m running Windows 2008R2
Hi,
Great article. It’s also possible to add wildcards to the targeting of the groups.
F.eks if you want the group “Workstation North Admins” to be added to the local administrator group for computers that start with the name “WS-NORTH-” then follow this procedure:
1. Click on the “Common†tab and then tick “Item Level Targeting†and click the “Targeting…†button.
2. Click on the “New Item†in the menu bar and select “Computer Name”
3. Enter “WS-NORTH-*” to the Computer Name field below.
This comes in handy when your domain computers have different names for each location.
Yes… Wildcards are very handy… of course you need to have a naming standard for your computers…
I originally thought that “BuiltIn\Administrators” in step 7 was a typo; as Jeff Harriss suggests, it doesn’t make sense to add the built in admin group to itself. So, when I used “BuiltIn\Administrator” (singular) I get the error that says “No mapping between account names and security IDs was done” (see Ivo’s post). Then I tried using the plural, “BuiltIn\Administrators”, and get the error that says “A new member could not be added to a local group because the member has the wrong account type” (see IanG’s post).
Following Jeff Harriss’ line of thought, I removed all membership entries and checked the boxes to “Delete all member users” and “Delete all member groups”. In theory one might think this would clear all entries in the Local Admins Group, thereby essentially locking everyone out. However, the built-in local Administrator account remained. This confirms Jeff Harriss’ assertion.
So, the entry in step 7 is unnecessary, even problematic. It seems to prevent subsequent member entries in the same preference item from taking effect, though I didn’t test further to isolate that behaviour. If nothing else, it just adds an extraneous error to the event log with each GP update. So, better to skip step 7 altogether IMHO.
Don’t get me wrong, though, this is otherwise a great post. It’s a novel idea to use an AD group for each PC (though I’ve decided to just stay the straight GPP route, putting all PC/user entries in a single GPO by using Item-Level Targeting). I greatly admire Alan Burchill’s body of work and knowledge he has contributed to the community!
Very interesting… this may explain the strange behaviou i have been seeing.. i will need to do some testing for myself. THanks
Looks like the “Stop Processing on errors” option is enabled even if the option is not ticked (see common tab)… I am asking the powers that be to see if they can reproduce this issue.
Super article. My only hesitation is that if I were to implement the individual Administrator group strategy for servers (workstations too – but I’m less worried about those), anyone who has the ability to create groups in Active Directory could simply grant themselves Administrator access to servers by creating the properly named group and adding themselves as a member. I was trying to see if there was a way to setup the targeting to check to make sure that the group is in a particular locked down OU rather than just anywhere in the domain. Does anyone have any suggestions on how to close that gap?
Good point… i never thought of that. If you did want the groups secure you could of course make them in advanced (at least for your servers) and then put them in a secure OU.
Alan:
I too am running Win XP Pro on my workstation & the AD server I am trying to get this setup on is running Win 2003 SE SP2. Can you elaborate on your suggestions made earlier:
You version of AD should be fine…
Things to check…
1. Do you have the client side extentions installed
2. Have you split the “%computername% administrator†preference item into a seperate setting?
3. Have you done a group policy results report agains the computer to see what is being applied?
I am unfamilier with ensuring the 3 items you mention.
Thank you in advance for your time in responding, I appreciate it.
Hi…this is Ajay.
I want to add domain user group to Local computer Administrators group using GPO or Script….
I dont want use restricted group in gpo…
Any suggestions
Thanks & Regards,
Ajay
How to use Group Policy Preferences to Secure Local Administrator Groups http://t.co/QDXzjHF
How to use Group Policy Preferences to Secure Local Administrator Groups http://t.co/QDXzjHF
RT @alexverboon: How to use Group Policy Preferences to Secure Local Administrator Groups http://t.co/QDXzjHF
Hi, its a good article but small remark: After settings this the “discription” is gone “Administrators have complete and unrestricted access to the computer/domain” 🙂
Hi Alan,
The article is really informative, but I am still fuzzy on a few details on how to create a GPP that adds a specific user to an individual computer that is applied to an OU containing workstations. The closest I have come to doing this is by creating a GPP that that has an altered user configuration and is applied to an OU containing users. I had the GPP add the current user logged in become part of the local admin group and set the GPP to apply once. It added the current user but only after a log off then on or reboot. To make matters worse, the next user I logged in with also was added to the local admin group on the workstation. I thought the GPP was supposed to be applied once! Is there a generic GPP that can add one user to the machine they are tied to and can be applied to a workstation OU? Or does this magical policy only exist in my imagination? Any help would be appreciated. Thank you!
@tom Add the GPP setting to add the group called “%computername% Administrator” then create a group in AD called “COMPUTERNAME Administrators” (substitute the actual computer name for the COMPUERNAME eg. “DOMAINNAME\WINXPPC01 Administrators”) then add the individual user to the AD group.
The magic is that GPP will automaticlly convert the %computername% administrator entry to the local computer name.
If that does not help feel free to ask for more help..
Hi Alan,
Thanks for the great article, it helped address one of our main issues with assigning local admin permissions before the days of GPP.
However, I am experiencing a slightly unusual problem that may or may not be related to this but I just wanted to know if you or anyone else had seen this before. The problem is after I’ve made a user a local admin by adding them to the “%computername% Administrators” group, the user gets local admin permissions and they can do the stuff that needs admin rights. However, there are a couple of things that don’t work, for example if I go to System in Control Panel I can’t open Remote Settings, System Protection or Advanced System Settings but I can open Device Manager without any issues. When I say I can’t access these items, I mean I click on the option and nothing happens, no error, no UAC prompt just nothing at all. If I logon as a different user that is assigned admin permissions in a different way (for example they are a member of a group that is added in the “first” local administrators GPP) then it works fine.
Hope this makes sense and I’d really appreciate any thoughts on why this happens and if anyone else has seen the same thing?
Thanks all
Mike
Alan,
Thank you so much for your response. Just to be clear though, this would require a group to be created for each individual computer, correct?
@Tom . Yes. However you only need to create the groups as required.
I was using restricted groups but I need to map one user to one PC as a local administrator, so I am using GPP. I guess I am missing something. I created the GPP “%computername% Administrators”. I created a group in the OU that that the PC resides named “computername Administrators” I added the user account to be a Member Of the group. It’s not working…No event viewer log entries, not adding anything to the local administrators group, no rights… Help!
I am using Windows 2008 R2 domain controllers, and Windows Xp clients with the Group Policy Extention patch installed.
Thank you for the great article. I am trying to add users from a different domain to the local administrator group. In GPMC, I can’t switch locations. Can I just type in the domain name followed by the user name? What exact syntax would be required? I don’t have access to the other domain but want to give a few of their people (help desk) local admin access to our computers.
DOMAINNAME\GROUPNAME however the Group will need to be universial otherwise it will not added to the local group.
That sounds easier. I created the Universal Security group and added it to the policy. Oops! I just realized, I’m not talking about adding people from a different domain… it’s a different forest. Big difference! How can I give people (help desk) from a different forest local admin access to the PC’s in our forest?
Hi Alan,
I have a requirement to lock down local users on a Windows 2003 Member server. It is a 2003 Domain environment.
Requirement :Local IDs in the server need to be lock down( Deny Logon Locally and Deny Terminal Services Logon)
Problem: Currently GPO enabled in AD to lock down DomainIDs so we are not able to edit GPO locally to add local IDs.
So need to find a solution to lock down local IDs without disturbing Domain GPO.
How can I achieve this without disturbing the existing Domain GPO
I would like to know if this can be achieved through GP Preferences or is there any other method to follow. And also please provide steps or any blog / link which helps me in detail to configure.
hi,
in a company we have AD with 3000 users, i want to use a policy that some specific users to be a local administrator of some specific computers, how could i do that,,/? i read “How to add individuals to a single computer?”, and i have a question, where we determine which user be an admin of which comuter?
thanks
Helen
@Helen when you setup the targeting of the policy use
if Computer Name = “COMPUTERNAME HERE”
AND if member of Security Group X
That should work… but i have never tried. Please tell me how it goes…
Hi Alan,
I have Smal query.. in my company i can see uwanted user are accessing the server .. i have planned everything and consolidate and made plan who going to access the server with admin permission . But I have come across one strange thing is all the server administrtor need admin access so i have created a security group for the same. and move all the member into that group to gain the admin access. now one more challange is i have some of the user to be given as power user access.. But in Buldin/ad i cant able to find the power user . so i can able to Puser the user vio GPo.. Can you advice me .. and correct me if iam worng in some way..
Thanks
vijaykumar.P
Alan,
With my GPP when I do created the security group I get eventid warning logged on the system. Is there anyway to avoid. I want it to skip and moveon without any signs of the group missing. Is this expected or how can I avoid? Am I doing something wrong.
Log Name: Application
Source: Group Policy Local Users and Groups
Date: 8/16/2011 2:19:20 AM
Event ID: 4098
Task Category: (2)
Level: Warning
Keywords: Classic
User: SYSTEM
Computer: xxxx
Description:
The computer ‘Remote Desktop Users (built-in)’ preference item in the ‘xxxxxxxx’ Group Policy object did not apply because it failed with error code ‘0x80070534 No mapping between account names and security IDs was done.’ This error was suppressed.
Thanks,
Andrew
If the group does not exist you will get this warning message… It is safe to ignore…
Hi I got a following error on my machines
The computer ‘Administrators (built-in)’ preference item in the ‘Default Domain Policy {31B2F340-016D-11D2-945F-00C04FB984F9}’ Group Policy object did not apply because it failed with error code ‘0x8007056c A new member could not be added to a local group because the member has the wrong account type.’ This error was suppressed.
Hope you could help me solve this…
Hi, I would like to thank you for your tip here..I did manage to use it however, the users in my local admin group cannot run the logon script which is also in my Group Ploicy…Howerver, those users outside my local admin group (the Doamin Users and Domain Admins) can run the logon scripts..I don’t know why this happens to the users who belongs to the local admin group..Hope you could help me with this…
Anyway, I manage to solve my previous post by not performing the Step 7…Thanks.. Great Work..:)
Alan,
I have not been able to get the “DOMAINNAME\COMPUTERNAME Administrators†piece to work. The entry does not appear in the Local Administrators group. Does the actual security group need to be created before it will appear?
I also get the following warning in the event viewer:
The computer ‘Administrators (built-in)’ preference item in the ‘testAdminGroup {1EC221BF-3E61-434D-817C-1C07EDA42FB1}’ Group Policy object did not apply because it failed with error code ’0×80070534 No mapping between account names and security IDs was done.’ This error was suppressed.
Yes. You need to create the group for it to be added to the local computer… the warning you get is expected if you have not created the group in the domain.
“Step 11. Go back and repeat steps 6 and 7 but this time add the group “%DomainName%â€\Workstations Administrators†in the name field. This will added the additional group “CONTOSO\Workstation Administrators†to the local admin group on all the workstations in your domain which will allow you to easily add all the Desktop Administrators in your organisation access to all the workstations without having to give them the local admin password or domain admin’s privileges.”
Just to clarify… I completed these steps. Now what name do I give this group? “Workstation Administrators” or is this created automatically and I just add the users. thanks for a great article.
You will need to create a group explictly called “Workstaiton Administrators”
Alan,
I have a question regarding inheritance of this GPP as it pertains to the updating of a built-in local administrators group.
Say we apply a GPP at the site leve to delete existing group-type members of the group and then to update the membership with the desired group-type membership. Let us also assume that a second GPP is applied at the OU level that is only configured to further update the membership of the same group.
Assuming a workstation is within scope of both policies, should the membership of the group in question contain the membership as configured in both the site GPP as well as the OU GPP or will the OU GPP override the configuration of the site GPP?
There’s a lot of “it depends” in that one, but the basic answer is this:
GP is applied in order, sequentially, from the base of the tree (domain level) to the ends of the branches (sub-OUs). To see the order of application of all your GPs:
1. From the Test Desktop/Workstation, open Command Prompt
2. Type (and press enter, afterwards): gpresult
a. Win7: Must be run with a Domain User with Local Admin rights. Also, the command is slightly different: gpresult /R
3. Look for: COMPUTER SETTINGS > Applied Group Policy Objects
a. This is a list of ALL GPOs that are in scoped and applied to this computer.
i. (non-applied GPOs will be listed after this section in the “… filtered out” section.
b. These GPOs are applied from the bottom of the list to the top.
i. This means that the GPO on bottom is applied first and the GPO on top is applied last.
ii. This means that the GPO on top overwrites the GPOs below it.
And there you have it! Now that I’ve taught you to fish, let me know what you catch!
Hi Alan, it’s a great article and we have already implemented this and worked a treat, till recently. This solution worked fine for XP machines. Recently we extended the same to WIndows 7 PCs. What we were noticing was that after a few days, the %comuptername%administrators group was getting stripped off the Builtin admin group of the PCs. Found a hotfix for that issue KB976399, which appeared to fix the issue. But it has come back, where people regularly loose access. What we do, is login as admin, force the gpupdate and then it seems to work. Is there an issue with WIndows 7 that we need to address. Will be happy to hear from you, as it is biting us hard now
Cheers
Thanks for the feedback… not that i have heard of… just make sure that the %computername% administrators group is in a seperate configuration item and not with other settings on the group.
Hi Alan,
Excellent article, a query if I may.
The local group will be created on the local computer once the preference applies, then will become active once an AD group is created with the accounts populated? Is this thinking correct. If so, you are my hero!
Regards
Stuart
@Stuart The local admin group is already created. If the domain group is not created then it will only give a warning in the event log. If the group is then created in AD it will be added at the next policy refresh on that computer. Hope it helps
Hi Alan,
Yes, I understand, but also i have now had chance to test, it works like a charm. Thanks for your help.
Can i ask how you cross domain groups from parent domains, to add them to child domains. I used to do this with restricted groups, but i believe that this can cause issues when applying local groups preference. Any help would be much appreciated.
Regards
Stuart
just specify the domain domain when adding it to the local group… .eg. DOMAINNAME\GROUPNAME
Hi Alan,
Do I need to specify this in the form of a variable, or actually specifying the name & group name?
Thanks Again.
Stuart
Hi Alan,
Quick query – step 7 – you seem to be adding the Builtin\Administrators group to the local Administrators group. Surely it should be a case of adding the Builtin\Administrator user account to the local Administrators group? By default the local Administrator user account should be in the local Administrators security group. Or am I missing something?
Cheers,
Rich.
Hi
I’m having problem to make WinXP to follow any GPO of this type (adding/updating/delete) local user accounts.
No problem with win7
Is there a limitation to OS version higher than?
any extra action required with WinXP?
On Win7 all I need to do is gpupdate /force
Kjell
Q1: Have you installed the Group Policy Client Side extentions…
Thanks Alan
thats it.
A combination of afraid of testing on our live WinXP, and to eager to run the testings, I forgot to add the extra stuff from Windows Update where the client side extensions are.
thanks for an excellent article
another detail.
when adding a GPO, test it, remove it, redo another, test it, I know getting half of it, Only BuiltIn\Administrators remains in my Local Admin Group, All other are always removed.
Do I have to reset the GPO handling in any way to get back on square 1 ? (so to speak)
Rgds
Kjell
Preference do not revert the configuration when you remove the settings. Therefore if you remove the policy the affect will be everything will stay as it was last configured… NOT revert back to original.
what ment was; I followed your example “Restricted Local Admin Group” by adding 2 modifications, and it worked just like described, excellent. then I removed the GPO, made a couple of other settings on the same thema, when I was done with my labb-work I wanted to re-do the original “Restricted Local Admin” as per your example. The result now is different; Only BuiltIn\Administrator makes it through a gpupdate /force, and that’s it.
The Domain\Domain Admins are being removed now from the local machine, I’ve re-created the GPO 2-3 times already following your description trying to see where I type wrong but I can’t make the GPO kick in correctly.
I will create a new VM and see if that one acts correctly.
Just wanted to check if anyone has seen this behaviour.
Kjell
I have seen that behaviour before if you are trying to add a user or group that does not exist. To work around this make them seperatem items and it should work…
Ok, I will labb on that.
In my case I tried with BuiltIn\Administrator and %DomainName%\Domain Admins just like your example above
Local Admins is making it, but Domain Admins is being removed as if they was not part of the GPO
If I find the workaround i will post here
Kjell
Not sure exactly what I did to fix it.
I noticed that the example stipulates BuiltIn\Administrators and when I think about it, it should be singularis form BuiltIn\Administrator. but, that alone did not fix the problem at once.
anyway; I also removed the BuiltIn\Administrator from the GPO and run gpupdate /force several times adding and removing other users in the GPO in between every gpupdate.
From that moment of removing the local admin everything went back to logical, the local Admin stays in the group event though it’s not part of the GPO declaration, now the group responds correctly.
When I finally added the local Admin to the GPO it’s still acting logical as it did the first time.
but now its in singularis form BuiltIn\Administrator
Kjell
Hi Alan,
Now we have 2 different administrator groups.
Why are we using 2 separate groups such as “Administrators (built-in)” and Administrators? Can we work only on default “Administrators” group?
Thanks.
John
You should only use the “Administrators (Built-in)” group… Not sure how you are getting a second group called “Administrators”…
I am having the same issue. Before I apply the GPO I only have the Local Group Administrators listed in Local Users and Groups. After I apply the GPO I have the Local Group Administrators and Administrators (built-in), and this built in group does not have admin rights.
For the GPO settings I selected Update and picked (instead of using the dropdown) the administrators group.
If I use restricted Groups works correctly and does not create Administrators (built-in).
Hi Allan…I was trying the steps you have provided to add a single or group of users from a domain to the computer’s local admin account. It didnt work….My main goal is to add a group of users from a domain and make them their computer’s local admin (as a part of our reqirements)…any other suggestions please let me know… Prior testing that, I did add a test computer to the “Test OU” and assigned a policy to that Test OU after following the steps mentioned….pls advice…
Things to check…
1. Does the name you are typing match a group that exists…
2. check the event log for warnings.
2. Are you adding multiple groups in the one policy setting… split them onto seperate entries
Feel free to send me an email via the contact form if you have any more detail.
Hi Alan,
Excellent tutorial, however, I did some testing on a laptop and it seems that the Group Membership is not equal to specifying the exact account name: once I applied the policy to a notebook outside the local network (over VPN), I could not successfully elevate my permissions with that account any longer. Is that an expected limitation?
Doug
Hi Doug…
Strange one… At a guese I would say that you may need to have logged on locally at least once for the caching of the credentials to work. Centainly appling the permission via a group you would have to log off and back on again after the setting has applied for the access to become affective.
Alan
Hi Alan,
I just wanted to give you an update on this. The problem I experienced was due to the credentials being cached. Once I log on at the office, my user gets the correct group memberships and things work as expected.
I did experience some additional frustration due to not following your tutorial EXACTLY as you have written it: setting the groups without using %DomainName% or letting the GPP editor specify the exact SID either do not work at all, or cause inconsistent behaviour (some of the GPP applies, some doesn’t).
I really enjoy your website. Thanks a lot for all the great posts, especially the ‘Best Practices’.
Step 7 makes no sense! You should add “BuiltIn\Administrator” and NOT “BuiltIn\Administrators”. Right?
@ThL yes i think you are right… i have update a text and put a note next to the images that are wrong. Thanks.
In my tests of the way Mr. Burchill wrote this up, BuiltIn\Administrators seemed to work just fine, the workstation’s local Administrators group included the user Administrator using only steps 1-8.
I have a part timer working with me. I don’t want him to have domain admin rights but I want him to be a computer administrator so he can do software installs, etc. Using the steps above 1-8 I was able to clean and secure the administrators group on the test computer. Besides builtin\administrators and domainname\administrators I also wanted this one person to be an administrator but it would not add him.
I created a second order group just as described starting in step 9, with only him being added, and it added him. I don’t understand why I had to do that. Any ideas?
@danielkr The second one is need for two reasons…
1. A bug if the group does not exist cause all the actions to fail
2. Group is MUCH better then ading a individual user as you can see the membership on the users account in AD… Otherwise it would be very dificult to audit and control this access, especially if the computer is offline.
Three corrections:
1) “make sure you have added back in the Domain Admin’s and Local Administrator groups” should read “make sure you have added back in the Domain Admins group and local Administrator”
2) “Image 3. Local Administrators group added to the local administrators group” should read “Image 3. Local Administrator added to the local Administrators group”
3) “only having the local Administrator and Domain Admin’s” should read “only having the local Administrator and Domain Admins”
I have just implemented some additional control using group policy preferences on our estate but have used the following method, but seem to be hitting problems with some machines.
A single restriced groups GPO specifying the central domain groups plus the local machine accounts we want to keep across the estate
We then have a number of GP Preference GPO’s which add a addition group. These are both secuirty and WMI filtered so they only target windows XP and certain machines based on group membership.
After initial testing this seemed to work fine, and gave us more granular control, however we get cases where GPP processes but the groups never appear, I have since re-ordered the GPO links so that the GPP additions should take presidence over the restricted groups. But I’m wondering if I should maybe ammend the policies so we just use GPP’s. I will see what happens now the order is correct however
Any thoughts?
Restricted group will take precedence… you will need to remove this setting if the GPP is going to work…
I am trying to setup the SQL example and getting an error of The computer ‘Administrators (built-in)’ preference item in the ‘Computer – SQL DBA Local Admin {88AA58D2-456F-48DC-8195-4B2E3EB8C527}’ Group Policy object did not apply because it failed with error code ‘0x80070534 No mapping between account names and security IDs was done.’ This error was suppressed. when i enable the targeting. if I remove the targeting the settings apply correctly. I have tried to replace your example path with %SystemDrive%\Program Files\Microsoft SQL Server and %SystemDrive%\Program Files(x86)\Microsoft SQL Server but that generates the same error. my domain and forest functional settings are 2008 R2 testing this on a win 2008 R2 server.
Sounds like you are trying to add a security group that does not exist… Are you sure the group you are trying to add exists? did you chose it from the group picker button?
If I wanted to give a domain security group access would I also just put that in the Members section of image 5?
I have a couple of new laptops in the office that I haven’t got to deploying yet, and after I did yesterday’s “Patch Tuesday” MS updates, both computers began to hang at user logon with “Applying Group Policy Local Users and Groups policy” (I have verbose messages enabled; I only use the Local Users and Groups policy on new computers not old ones already in the field). They sat for well over 10 minutes and go nowhere. Multiple reboots resulted in the same thing happening over and over again. If I pulled the LAN cable, they could logon okay.
My Google searches turned up no useful results, so I decided to apply all the “Patch Tuesday” patches on my DC and restart it. After that, subsequent reboots on the laptops seemed to be alright, and I did ‘gpupdate /force’ a couple times to make sure they took the policies from scratch. Again it seemed to return to normal behaviour.
This occurrence makes me nervous though – has anyone else experienced this type of behaviour when using GPP Local Users and Groups?
Can we use preferences to add a group from an other forest tol the Local Administrator group. When I am look at Locations I only see the local domain. Trying with “domain\Group” does not work
https://www.grouppolicy.biz/2010/01/how-to-use-group-policy-preferences-to-secure-local-administrator-groups/
Alan,
Thank you for your very educational post.
In your scenario, do we have to create separate gpp for each PC if we want to specify DESKTOPxx Administrators? i.e. gpp1 for adding DESKTOP01 Administrators to DESKTOP01, and gpp2 for adding DESKTOP02 Administrators to DESKTOP02 and so on? Is it possible to create only one gpp, and it adds DESKTOP01 Administrators to DESKTOP01, DESKTOP02 Administrators to DESKTOP02?
Also, your scenario can be achieved by using gp restricted groups, and I cannot see any advantage by using gpp in this instance?
Looking forward to your reply.
I can answer my own questions now.
Firstly, just need to use Item-level targeting, and target computer’s DNS name. This will identify the PC, and is able to add DESKTOP01 Administrators to DESKTOP01, and adding DESKTOP02 Administrators to DESKTOP02
Secondly, using GPP is better than using gp restricted group in this instance. I created local user account(user configuration–preferences–control panel– local users and groups–, then I add this local user account to the builtin-administrators. So I don’t need to create global security group anymore.
This way, I can achieve in one GPP, adding global security group domain admin/desktop admin for all PCs, then target individual necessary PCs to grant them a unique local user account with administrator right.
This works well for big organisations. We need to have control of all PCs. But there are always a few users need admin rights on their own PC.
My experience is this:
We get an error in the event log if we add BUILTIN\Administrator (without the ‘s’) as described in step 7
This is the log entry:
The computer ‘Administrators (built-in)’ preference item in the ‘Win7-EC-Computer-v1.0 {GUID}’ Group Policy object did not apply because it failed with error code ‘0x8007056c A new member could not be added to a local group because the member has the wrong account type.’ This error was suppressed.
0x8007056c A new member could not be added to a local group because the member has the wrong account type.
It seems that either of the following is the case: 1) The local admin account can’t be deleted from the Local Admins group or 2) When it tries to add BUILTIN\Administrator, it fails because the account already exists.
When we remove BUILTIN\Administrator from the GPP the error goes away AND the local administrator is NOT removed from the Local Admins group.
Is this anyone else’s experience?
Phil,
YES. This is exactly what we are experiencing.
I would like to stop users from adding the Domain user to the local administrators group of their pc’s. Can this be done with GPO’s?
This method does not STOP them from doing that… however in 2 hours any non-authorised users and groups will be removed. The only way to prevent this from happening it to remove them from the local admin group.
I have tried and tried to get this to work in my test lab but it simply will not.
I am trying to add a domain group to the built in administrators group using %domainname%\groupname using the group update option.
The description of the group local administrator group updates but the group is not added.
The group exists and the name matches.
If i try to add the group manually it states that it is already a member.
However, despite it claiming the group is already a member it does not give admin privs to users who are a member of the group…
I can then re apply the policy but specify remove after which i can manually add the groups but as soon as i hit apply they are removed from the list of members and still i dont get the correct permissions….
Whatever i did wrong it appears to have completely screwed the local administrators group on both my test machines.
Group policy reports no errors
Rebuilt test environment and tried again. Same result
It no longer prompts me for an admin account but after selecting yes to elevate it presents an error:
Windows cannot access the specified device, path, or file. You May not have the appropriate permissions to access the item.
Change the policy to remove the group just added and back to prompting for admin cratentials…
pretty much the same experience as above. I cannot get the %DOMAINNAME%\%COMPUTERNAME% variable to work. Tried it with and without the AD groups being available for each computername. Whatever I try the group is not added to the local admin group on each computer.
This concept is great and would save a lot of messing around plus provide a more managable alternative to Restircted Groups. Trouble is it just doesn’t work reliably enough to use. Big Shame!!!
@Phil it is going to fail if the group does not exist in AD. Took me a while to understand this.. but once I got it, it was a brilliant idea.
@Phil – if that’s the case, in large organizations it is not practical. You cannot create a group for every client machine.
I’ve implemented this for all of our servers with about 30 different scenario’s based on the computer accounts group memberships, LDAP and WMI Item Level Targeting… and this has worked great for for the last 6 months. I have the 1st item in the list perform a delete all member users\groups as well to keep rouge accounts from being added (enabled for 4 months).
Now, 4 months in, I am starting I got my first complaints that we may have an issue with that delete all member users\group step… What is allegedly happening is that during the 25 seconds it takes to run this policy on the refresh intervals (every 90 minutes), a job is kicking off and failing to log in because the memberships were removed and in the process of being re-added, and the account which runs that job is in one of the managed groups… Has anyone else come across anything like this? Anyone have this many different scenario’s\order items and how long does it take for the policy to process on one of your Win2K8 servers?
I have the same issue as Kris, following this guide to the letter all members of the local adminstrators group are deleted but Domain Admins is not placed back in as a member of the local admin group.
Hello Kris – did anyone get back to you on this one as I am having the same issue. This is a great article and I’m hoping Alan is still checking this for updates and it works beautifully except for those few seconds it takes the GPO to remove the groups and re-add them. Thank you.
Hi,
This works well for its intended purpose. However, according to our policies, the machine administrators are not allowed to know the built-in local administrator password. They are required to log in using their own credentials. We have about 1800 machines spread across the country. In the event that one of them no longer has trust with the domain or one of them drops off the network completely, our administrators are not able to log on loacally because they would never have logged onto the machine before. Is there any way to get around this? Is there some way to force password cache onto the machines to avoid this situation?
Alan,
I like this article and find that it is a much better solution than using restricted groups ;however, just a couple of thoughts.
Could you re-do the article so that the correct images and correct spelling is shown rather than amending or noting changes. It is a bit confusing.
Lastly, could you clarify the creation of “DOMAINNAME\COMPUTERNAME Administrators†I am total confused on this last part. Will these groups need to be created in AD for every machine on the network?? I have over 3000 machines in my enterprise. Please elaborate more on these last few steps, because we do need to have certain users have local admin rights to certain machines.
Alan,
Not sure if you are still monitoring this thread when for people posting questions (i hope you are).
Here is the issue i am running into:
1 – I was able to follow all the steps from 1 through 10.
2 – The GPO changes did correctly remove any existing single users accounts being setup as local admins or other groups i added for testing.
3 – It only added the domain admin and the local administrator group back on, BUT not our HelpDesk AD group
So, for our needs i need the GPO to ensure it removes anything/everything but Domain admin, local administrator (BUILTIN) and the “Helpdesk” group. I have tested on 3 Windows 7 machines and each time the same result??
Also, the later section explaining how to be able to add individuals as needed….i just dont understand it can it be explained again but a bit more clearly.
Hi Mike
How are you specifying the Help deskgroup…. is it “GROUPNAME” or “DOMAINNAME\GROUPNAME”. Also check the event log to see if you are getting a event log warning about it unable to find the security principal. It should happen every GP policy refresh.
Individuals should be added to the computer via the “%computername% Administrators” group. This group should be a domain group and the first part of it needs to match the name of the computer. You can then add/remove users from this domain group to grant them individual local admin access.
Hi Alan,
I am specifying the HelpDesk group in the newly creatted test GPO as follows (tried a couple of things to see if any would work)
“DOMAINNAME\HelpDesk” & ““%DomainName%\%HelpDesk%.
Neither option made a difference.
I also checked the eventlogs and it does not throw any errors. It actually says it applied x gpo updates etc.
Lastly, as it relates to the adding users you are suggesting i create a domain group for each domain computer that may need domain users added as a local admin. The group would be something like “IT-Laptop Administrators”. Subsequent additions/deletions will be managed via this domain group.
hi
tanks
Best Practice: How to use Group Policy Preferences to Secure Local Administrator Groups http://t.co/QPlJRH5A via @alanburchill
Hi!
Thanks for Nice article and having so much information related to GP on your site.
I saw different effect after having the policy. Sometime i can only see on group and some time all three. After mapping the same settings and order of Members group i was able to push the group via the policy.
http://www.virtuallyimpossible.co.uk/using-gpo-to-control-local-administrators-group/
Now In my case we have different servers used by people from different location. What we want is that they should not be able to made any local user on some machines and even not able to add those local user to admin group.
This works well as after the policy refreshes the unwanted user will be gone but I am thinking about the implementation.
1. I should create a security group (Adminsecurity) and add users from other offices to it.
2. Use the Restrict-admin group policy with the mentioned group(builtin-admins,domain-admin and AdminSecurity ).
3. Create another Security group (Secure-LocalAdmin-Server) and add all the machines which are used by other location users to it
4. Apply the group policy to only Secure-LocalAdmin-Server
Something like that. Any help will be appreciated.
/C
beautiful – did this and domain admin group didn’t show up. so when I login and try to add domain admin group to local admins group it F*&^*%* FAILS. log in as domain admin – f@#%$$#^ fails. how in the f$#^%#$ am I supposed to grant privileges???
Wow, guys, this works great. This clears up all those user Windows workstations that have so many departed users as local Admins. This article is a security lifesaver.
Thanks for this!
Didn’t quite work well for me as in the write up so I made the following changes.
I had to create separate entries for each user/group, since some of the computers on my domain don’t have said accounts/groups and the policy stops processing if it runs into an error or a local account/group that is non existent on the computer.
I omitted builtin\administrator as it did not work and instead used %ComputerName%\administrator. Also since the Administrator account is locked by nature I create a new local user and make them part of the builtin\administrators group, set a password, and other options.
Also noticed that there is no mention that only the #1 order policy should have “Delete all member users” and “Delete all member groups” checked off. Either that or I missed it. This is important as these policies get applied as they are ordered 1,2,3… etc. So if all the policies have this checked off each new policy will clear the previous, provided you have a separate policy for each group and account as I do.
Thanks
Hi Alan,
I work for a school and each student has a computer which is joined to our domain. So far, we gave them local admin rights manually.
I would like to manage this by using a GPO on Student OU but according to your article, I have to create a group for each computer and that means I have to create thousands of groups. Am I right? I just feel like creating so many groups is too much load on my DC. Is there any alternative ways I can follow? What would you advise me? Thanks a lot.
Selim, you don’t have to I just solved this problem today. I was running into the same issue as you were with Alan’s way you would have to manually add things here and there so I sat down and got the gears turning.
My environment consists of Server 2008 R2 and Win 7 machines and I have a working policy with which I can apply Local Admin privileges for any computer and any user, and if anyone else tries to add another user to the Admin group at next policy update they get removed.
In my first 6 orders I add members to the Administrators (built-in) group, Domain Admins, Domain Accounts, and some local accounts. The reason I have so many orders is because I found that if anything goes wrong in the policy when it is being applies, such as a non existing group or account it will stop executing, it will error out and move on to the next order. Hence 6 orders/policies to add users and groups to the Administrators (built-in) group.
So to solve my problem I was having with granting Local Admin to a single user on a single domain I did the following;
What I did was in my 7th order, I created a new group and all this does is rename the Administrators (built-in) group to %ComputerName%.ADMIN without any members. I tried doing this in the 1st order where I add “%DomainName%\Domain Admins” members to the Administrators (built-in) group but something was going wrong and it was only renaming the Admin group and not adding the members.
By renaming the Administrators (built-in) group to %ComputerName%.ADMIN each computer on the Domain gets a unique Administrators group, something like DMCL-00203.ADMIN.
In the 8th order I created a new group with the Group name: DMCL-00203.ADMIN, do not use the Administrators (built-in), then I added members %DomainName%\UserId, UserId being a valid network identification. If I want to add local admin to another computer I create a new group with the appropriate group name, for instance DMCL-00144.ADMIN and add appropriate members. So now I can add any computer to this and assign individual local administrators and let’s say network account that has local admin on computerX will not have local admin on computerY, and I can do it all remotely.
You may want to consider adding somewhere in your article that this only applies to Server 2008 and later.
Hi Hoss…. Actually… this will work with Windows XP and Windows Server 2003. You need to install the client side extensions for those platforms and then this feature will apply to those OS’s…..
too bad there are no “OU Variables”..it could’ve saved a couple of extra GPOs.
DO NOT DO STEP 7!!!!! In my domain it would not allow us to update a builtin account (builtin\administrator) so NONE of the Updates were applied. I removed the GPP because I thought it wasn’t working, and because I’d selected ‘Delete all member users / groups’ I was left with no admins on the machines at all. Took me hours of tinkering with GP / GPP to get it working.
As mentioned in the guide: ensure you don’t have any restricted groups applied in GP. DO NOT try to add in ‘BUILTIN\Administrator’ as it can cause an error. Oh and make sure you test this thoroughly against your own machine ONLY first. May have taken hours to sort but it’s doing it now, and I know this inside out.
I have a many-to-many relationship I’m trying to solve. I have AD organized by sites, with the servers under each site (domain > site > Servers). What I would like to be able to do is assign Admins based on their site via GPO. Your article above is very helpful, as I had never thought of wildcards as an option there.
But what I want to be able to do is have a GPO (GP-site1-Admins), and then assign it to domain > site1 > Servers to assign local admin rights with restricted groups. And I have a lot of sites.
I can create GPOs for each site with powershell, and then assign them to the OUs with powershell, but then I think I need to manually update each GPO. It would make a lot more sense to me if I could get the GPO to “adapt” to the OU structure, but I can’t see how to do that. Any suggestions?
There is no variable that can be used for AD Site or OU’s in Group Policy Preferences…. You might have to do a separate GPO per Site the site based security groups.
I thin Item-level targeting might help you with this. You can target specific security groups or computers. Alternatively you can create security groups and make the servers members of these, then targeting your GPO to apply to said groups.
Since last year I have revised my AD skills and I have found a quicker and easier way to add users to the local Administrators group on a domain. Currently I am using Item-level targeting. I did a write up on this on my blog, head over here for the full instruction set for this: http://nerddrivel.wordpress.com/2014/07/24/item-level-targeting-use-gpo-to-set-user-as-a-local-administrator-on-a-single-computer/
Hope this helps someone.
Hi there to every body, it’s my first pay a visit of
this blog; this weblog carries remarkable and truly fine stuff in favor of visitors.
Like a machine, the human body is made up of many systems,
all of which are responsible for completing specific tasks.
So the best diet to lose weight is one of good nutritional food, amounting to only the calories that your body needs.
” The healthiest diets excluded meat, fish, and dairy products.
A Greek chorus of historical figures, including Leonardo da Vinci and 19th-century politician Giuseppe Garibaldi, add rueful comment
on the characters and their troubles while arguing about Italy’s distressing current state of affairs.
But television do not provide the same pleasure of watching a movie
as does movie theatre with its huge screen and surround sound system.
In some cases, surround sound is not possible in low frequency;
however, it is not the case with Panasonic SC-PT480EB-K.
Here is my website – Nos pires voisins Film complet
The result, 99% of them will struggle, get frustrated and
quit. Other tasks include preparatgion of plan charts, coordinating field trips, individuallly assessiing the children’s development, and informing the parents of
their child’s progress. APPED ‘ Artists, Promoters, Producers, Event Planners and Directors.
It’s a shame you don’t have a donate button! I’d most certainly donate
to this brilliant blog! I suppose for now i’ll settle for bookmarking and adding your RSS feed
to my Google account. I look forward to new updates and will
share this website with my Facebook group. Chat soon!
Feel free to visit my blog post … kinky pics
Wow, amazing blog layout! How long have you been blogging for?
you make blogging look easy. The overall look of your site is magnificent,
let alone the content!
Very good blog! Do you have any tips for aspiring writers?
I’m planning to start my own blog soon but I’m a little lost on everything.
Would you propose starting with a free platform like WordPress or
go for a paid option? There are so many choices out there that I’m completely overwhelmed ..
Any recommendations? Thank you!
In order for one to input the codes each note needs to be strummed.
5) Maintain i – Device hooked up (or maybe fb consideration signed throughout).
As a separating shot here are the words associated with super-star Whoopi
Clooney: I demand clash of clans hack, nothing a lot more nothing less.
I just can’t seem to be able to get this working!!!! I’m doing something wrong, that’s for sure!
I have 2/3 of this working. I cannot get the Domain Admins to populate. The Domain Admins group resolves with a SID when I add it to the group policy, but it wont populate the BuiltIn\Administrators groups on my test server…
Any ideas?
I know this is an old topic, but to make this work with Windows 10, I couldn’t pick Administrators (build-in) from the drop down. I had to actually type in Administrators for Group name. Then everything seemed to work.
I am unable to add Local Administrators using %DomainName%\%ComputerName% Administrator variable. I have the groups created in the Active Directory. Yet gpupdate /force doesn’t populate the group. Any ideas for troubleshooting this?
Check the event log to see if there is a warning about not being able to resolve the group name… if it is there the GPO name does not match the group name.
This is a great solution however I dont’ see anything about Local id’s or groups being controlled in this manner. For example. I may have a local service account that needs to be in the local admins, If I apply this solution , won’t it be removed from local admins ? I can’t add it to the domain group because it’s local to the server.
FYI – my main goal is to prevent users from adding other users to Local admins without proper authorization . I just dont’ see how this is going to o affect the local users\groups that may need Local admin access. Any Advice ?
“However the CONTOSO\DESKTOP01 Administrators group will only be added to the local administrators group on the computer DESKTOP01 if that group is already exists. Therefore you do not need to create the group until the need arises to add an individual user or group to just a single computer.” ….
If the group doesn’t exists in AD , there is an alert in PC application event log.
http://www.eventid.net/display-eventid-4098-source-Group%20Policy%20Local%20Users%20and%20Groups-eventno-11122-phase-1.htm
I did not analyze how it influence group policy application, but find out, that at least all membership rules listed below this rule are not applied. (I guess because “Local users and groups” preference just failed in case of non existing AD object).
Membership with possible not existing AD group should be listed most down in the list.
I did not find any another side effects of trying manage membership of non existing AD object, only the issues mentioned above.
Hello,
We created the policy to Change the password of local administrator User account and create an security account and add our all servers to part of that account.
and it worked in Win2k3 (after apply the patch and reboot)
Win2k8 –klist -lh 0 -li 0x3e7 purge and it worked without reboot
Win2000 – after reboot the servers, password not change (ANY HELP)
Win2k12 – run the “klist -lh 0 -li 0x3e7 purge” , even GPO was updated successfully but ” The computer is a part of the following security groups” is not updated which is the reason, password not changed
Can you please help me how we can update the Security Group without reboot for Windows 2012 Servers
any help highly appreciated..!!
Such a lovely info thanks for sharing.
i totally understand this concept. BUT, other keep talking about “Restrictive groups” is the WAY to go.. and i’ve found that when you add “Administrators (buit-in”), that adds them to the Active Directory Administrators group, same group domain admins get their rights from.. NOW those users have domain administrator rights too!!
You way here, set them on local administrator on the PC, not the domain Adminstrators group. THANKS
Great article and thank you very much. I did however need to specify “Administrators” and not “Administrators (built-in)” in step 4.
So I’m having some trouble with this GPO – Its not adding the DC Admin or the workstation Admin groups.
I found a post saying that step 7 is wrong and I see a bunch of Group Policy errors in my event viewer, not to mention I’m locked out of my computer 🙂 – but if I create a group called computername\workstation Administrators then and add myself to it I get admin access back – Hmmm
The post I found -> https://community.spiceworks.com/topic/1475990-variables-not-working-in-ad-local-admin-gpo
Will removing Builtn\Administrators fix the problem Yes/No
dimforest
Cayenne
OP
Best Answer
dimforest Mar 4, 2016 at 10:26 AM
Found the problem – you DO NOT need to specify adding BUILTIN\Administrator. Regardless of the fact that you check both of the boxes, the BUILTIN\Administrator account will remain. Credit to this post I found in the above link’s comments:
“I originally thought that “BuiltIn\Administrators†in step 7 was a typo; as Jeff Harriss suggests, it doesn’t make sense to add the built in admin group to itself. So, when I used “BuiltIn\Administrator†(singular) I get the error that says “No mapping between account names and security IDs was done†(see Ivo’s post). Then I tried using the plural, “BuiltIn\Administratorsâ€, and get the error that says “A new member could not be added to a local group because the member has the wrong account type†(see IanG’s post).
Following Jeff Harriss’ line of thought, I removed all membership entries and checked the boxes to “Delete all member users†and “Delete all member groupsâ€. In theory one might think this would clear all entries in the Local Admins Group, thereby essentially locking everyone out. However, the built-in local Administrator account remained. This confirms Jeff Harriss’ assertion.
So, the entry in step 7 is unnecessary, even problematic. It seems to prevent subsequent member entries in the same preference item from taking effect, though I didn’t test further to isolate that behaviour. If nothing else, it just adds an extraneous error to the event log with each GP update. So, better to skip step 7 altogether IMHO.
Don’t get me wrong, though, this is otherwise a great post. It’s a novel idea to use an AD group for each PC (though I’ve decided to just stay the straight GPP route, putting all PC/user entries in a single GPO by using Item-Level Targeting). I greatly admire Alan Burchill’s body of work and knowledge he has contributed to the community!”
Please get a copy editor with an English Degree. Your grammar and misspellings are ruining my ability to read your blog.
I strugle with english… Ironiclly becuase its my primary and only language I know. If i had a budget of more that $0 for a copy editor then i would look into it. Sorry you find it hard to read along, but as you might have noticed i try to also add a lot of visual elements to make it easier to follow.
Works great… have to read between the lines a bit but I managed to get it working after a couple hours of experimenting. Much better solution than restricted groups because I want the ability to give a user local admin only for a particular workstation and that is limitation of restricted groups whereas this method makes it possible.
Hi Alan,
Thank you for the information and guidance, however, I am not sure if I’m doing this correctly. I follow exactly what you have mentioned above, but it didn’t work for me, perhaps can you guide me?
Hi Brian, will you be able to guide me? I’m stuck still 🙁
Frank Lundemo says:
17/08/2017 at 10:38 pm
Great article and thank you very much. I did however need to specify “Administrators†and not “Administrators (built-in)†in step 4.
I second this. The only thing this would do with “built-in” was remove anything already in the group but would NOT add anything to the group. Typing in “Administrators” instead of selecting from the list of “built-in” accounts worked perfectly. I am doing this on server 2019. Same thing on 2016
Architectural science research paper services have become very popular for students studying architectural science coursework writing services as they engage the best online Architectural Science Writing Services.
We implemented this as described, but consistently got the error ‘The computer ‘Administrators (built-in)’ preference item in the ‘[Group Policy Name & ID]’ Group Policy Object did not apply because it failed with error code ‘0x80070534 No mapping between account names and security IDs was done.’ This error was suppressed.’
This is because of the ‘BUILTIN\Administrator’ entry. We renamed this to just ‘Administrator’ and everything now works.
This method (with a few modifications) also has official Microsoft approval: https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/using-group-policy-preferences-to-manage-the-local-administrator/ba-p/259223
Fantastic article, one I use at every place I’ve worked.
A number of people complain about the fact that you get 4098 Event Log errors from ‘Group Policy Local Users and Groups’ along these lines if the ‘%ComputerName% Administrators’ group does not exist:
The computer ‘Administrators (built-in)’ preference item in the ‘New Group Policy Object’ Group Policy Object did not apply because it failed with error code ‘0x80070534 No mapping between account names and security IDs was done.’ This error was suppressed.
I found you can fix this by enabling ‘Item-level targeting’ for the ‘%DomainName%\%ComputerName% Administrators’ entry, and putting a ‘WMI Query’ entry as follows:
Query: SELECT * FROM Win32_Group WHERE Domain=”%DomainName%” AND Name=”%ComputerName% Administrators”
Namespace: Root\cimv2
(Property, Environment variable name: leave blank)
This checks whether %ComputerName% Administrators’ exists as a group before applying that item, and if it doesn’t, suppresses the error.
Dear Alan, I created a OU in my Test Lab Domain. Applied and Enforced the policies as shared above for adding Individual Users to the specific Domain Computer on the OU created. Created a Security Group –>Group Scope as Domain Local –>Group Name as TestVM01 Administrators–>Added TestUser as Member of the Group.
As checked the policy is reflecting on my TestVM01 Computer but I cannot see TestVM01 Administrators as members of the Administrators Group. Can you please suggest what I am missing here.
Hi Alan,
Great article. On query. I have more than 300 OU’s on which I need to configure a domain group to be a member of the local admin group. 300 OUs have 300 groups. The groups are created. It is uite time consuming to confougre the OUs. Is ther ea way to script this, perhaps use powershell?
Hello,
Thanks for shareing this information. it’s very helpful for me. can you please help me to set veriable format –
I have a local user “India” which iis created on Client PC. Hostname of that Client is – CLIENT2 and domain name is INFRA.COM –
I want to add only local user “india” to local administrators groups (Local administrators groups which is on CLIENT2) via GPO. Kindly help me to create on %DomainName%\%Conputername%\username.