Recent Posts
Remote Server Admin Tools Now provided in Windows 10
If you have followed this blog you would know that the Remote Server Admin Tools are an essential set of tools for managed Group Policy, Active Directory and almost all other core components of Windows Server. These tools can be installed on demand if you are running Windows Server. But if you wanted to do the remote management from a…
Changes to how the Start Menu is Managed using Group Policy
Matt Call from Microsoft has just blog the different with describes the impact of no longer being able to customise the Windows Start menu using the Default Users Profile. In case you did not know you could previously set a users start menu by baking the layout into the Windows OS image default users profile by using a CopyProfile process….
Windows 10 1803 Group Policy and Security Baseline Template
The latest version of the Windows 10 1803 security templates have been released to the public. These are the new Microsoft recommend guidance for securing Windows in an organisation. These settings are normally tighter than the Out of the Box settings, but are normally acceptable in a workplace environment. Historically these used to be available via the Microsoft Security Management…
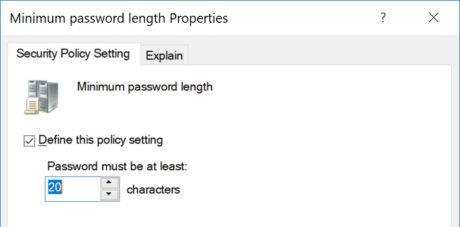
Group Policy Updated to support 20 Character Minimum Password Length
Until recently it was not possible to set the default domain password length via GPMC to anything longer that 14 characters (see below). This limit was enforced via the UI but it was possible to set a password value longer manually if the user chose a longer password. Most likely the reason that this limit was enforced was that the…
Remote Server Admin Tools for Windows 10 1803
Microsoft has now release the production version of the Remote Server Admin Tools. These are of course the essential tools that for managing Group Policy (and many other server functions). As I always remind you it is imperative that you always have the latest version of GPMC as this is the most current version of the Group Policy tools. You…
How to fix SearchOCS.ADMX Error after upgrade to Windows 1803 ADMX files
With the recent release of the Windows 10 1803 Microsoft also released a new version of the ADMX/ADML files that corresponds to the new Group Polices with the OS (see https://www.grouppolicy.biz/2018/05/administrative-template-for-windows-10-1803/ ) . Normally upgrading these policy files are as simple overwriting them into your “PolicyDefinitions†folder in your SYSVOL. However the SearchOCR.ADMX file that is not part of the…
Administrative Template for Windows 10 1803
With every new version of Windows Microsoft releases more Group Policy settings to support newer features. Ever since the release of Windows 7 all the new Group Policy settings have been exclusive released as Administrative Templates. These Administrative Templates (a.k.a. ADMX) files are text files that are used to define the Group Policy Administrative Template settings. There are always two…
What is Windows Admin Center
Have you ever found it hard to figure out what tool you need to manage Windows, sometime it’s an MMC other times you need to go via Control Panel or you need to launch Server Manager? To help with this Microsoft has now released Windows Admin Center so that IT admin can now use a single UI pane to manage…