![]() One strange thing that still seems to catch a lot of people out is that you can only have one password policy for your user per domain. This catches a lot of people out as they apply a password policy to an OU in their AD thinking that it will apply to all the users in that OU…. but it doesn’t. Microsoft did introduce Fine Grain Password Policies with Windows Server 2008 however this can only be set based on a security group membership and you still need to use the very un-user-friendly ADSI edit tool to make the changes to the policy.
One strange thing that still seems to catch a lot of people out is that you can only have one password policy for your user per domain. This catches a lot of people out as they apply a password policy to an OU in their AD thinking that it will apply to all the users in that OU…. but it doesn’t. Microsoft did introduce Fine Grain Password Policies with Windows Server 2008 however this can only be set based on a security group membership and you still need to use the very un-user-friendly ADSI edit tool to make the changes to the policy.
Below I will go through how you change the default domain password policy and how you then apply a fine grain password policy to your environment. The Good news is setting the default password policy for a domain is really easy. The Bad news is that setting a fine grain password policy is really hard.
Update: If you want to set a password complexity setting that is not supported out of the box of windows then it is possible to install a third-party DLL on you domain controllers to achieve this. However there are many caveats to this and it is best you check out the full explanation at http://blogs.technet.com/b/askds/archive/2011/08/05/friday-mail-sack-beard-seconds-edition.aspx#password
How to set a Default Domain Password Policy
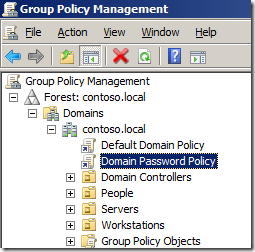
Step 1. Create a new Group Policy Object at the top level of the domain (e.g. “Domain Password Policyâ€).
Note: I have elected to create a new GPO at the top of the domain in this case as I always try to avoid modifying the “Default Domain Policyâ€, see references below.
Reference
If you need to modify some of the settings contained in the Default Domain Policy GPO, it is recommended that you create a new GPO for this purpose, link it to the domain, and set the Enforce option.
TechNet: Establishing Group Policy Operational Guidelines
Do not modify the default domain policy or default domain controller policy unless necessary. Instead, create a new GPO at the domain level and set it to override the default settings in the default policies.
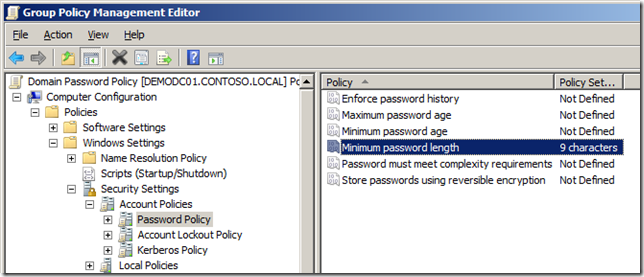
Step 2. Edit the “Domain Password Policy†GPO and go to Computer Configurations>Policies>Windows Settings>Security Settings>Account Policy>Password Policy and configured the password policies settings to the configuration you desire.
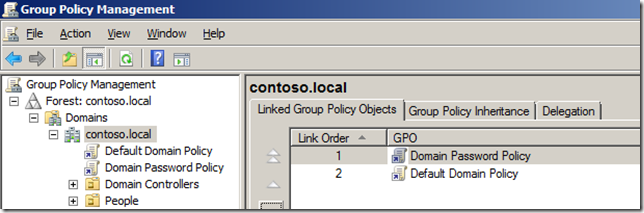
Step 3. Once you have configured the password policy settings make the “Domain Password Policy†GPO the highest in the Linked GPO processing order.
TIP: Make sure you inform all your users when you are going to do this as it may trigger them to change their password the next time they logon.
Done… told you it was easy….
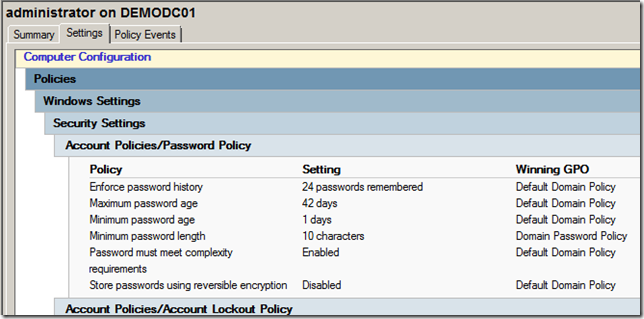
Note: Even if you apply the password policies to the “Domain Controllers†OU it will not modify the domain’s password policy. As far as I know this is the only exception to the rule as to how GPO’s apply to objects. As you can see in the image below the “Minimum password length†in the “Domain Password Policy†GPO is still applied to the domain controller even though I have another GPO linking to the “Domain Controllers†OU configuration the same setting.
For a better explanation as to why the GPO that is linked to the Domain and not the Domain Controllers is used for the password policy for all users check out Jorge’s Quest for Knowledge! – Why GPOs with Password and Account Lockout Policy Settings must be linked to the AD domain object to be affective on AD domain user accounts
How to set a Fine Grain Password Policy
Fine Grain Password Policies (FGPP) were introduced as a new feature of Windows Server 2008. Before this the only way to have different password polices for the users in your environment was to have separate domains… OUCH!
Pre-Requisites/Restrictions
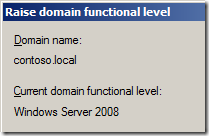
You domain must be Windows Server 2008 Native Mode, this means ALL of your domain controllers must be running Windows Server 2008 or later. You can check this by selection the “Raise domain functional level†on the top of the domain in Active Directory Users and Computers.
Reference
AD DS: Fine-Grained Password Policies
The domain functional level must be Windows Server 2008.
The other restriction with this option is that you can only apply FGPP to users object or users in global security groups (not computers).
Reference
AD DS: Fine-Grained Password Policies
Fine-grained password policies apply only to user objects … and global security groups.
TIP: If you setup an “Automatic Shadow Group†you can apply these password policies to users automatically to any users located in an OU.
Creating a Password Setting Object (PSO)
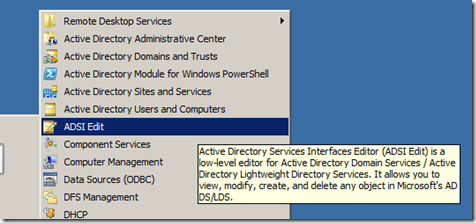
Step 1. Under Administrator Tools Open ADSI Edit and connect it to a domain and domain controller you want to setup the new password policy.
Note: If you do not see this option go to “Turn Windows Features On or Off†and make sure the “AD DS and AD LDS Tools†are installed. (You will need RSAT also installed if you are on Windows 7).\
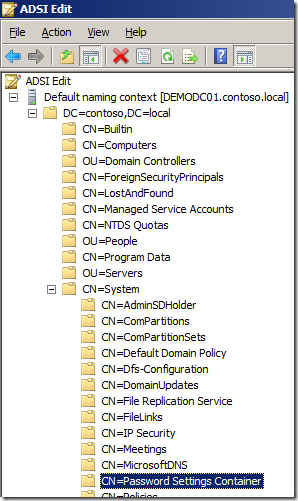
Step 2. Double click on the “CN=DomainName†then double click on “CN=System†and then double click on “CN=Password Settings Containerâ€.
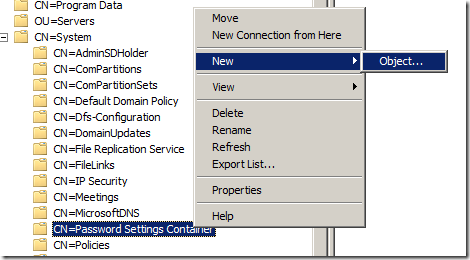
Step 3. Right click on “CN=Password Settings Container†and then click on “New†then “Object…â€
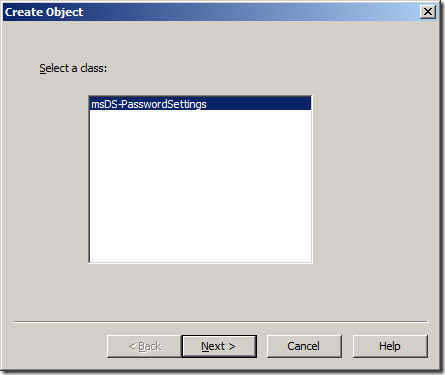
Step 4. Click on “Nextâ€
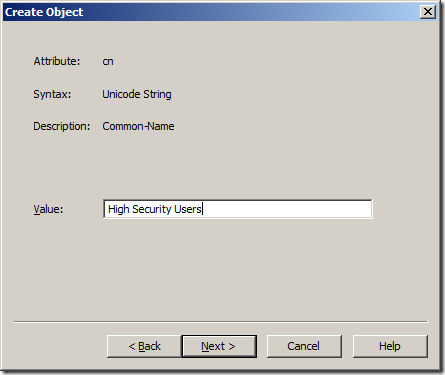
Step 5. Type the name of the PSO in the “Value†field and then click “Nextâ€
Note: With the exception of the password length the following values are all the same as the default values in the “Default Domain Policyâ€.
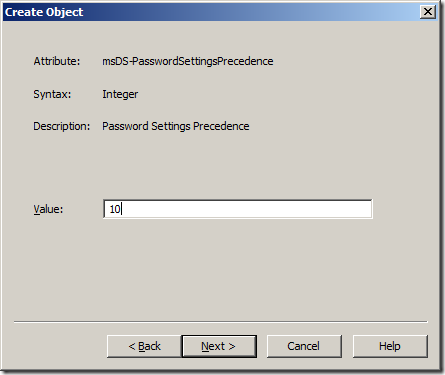
Step 6. Type in a number that will be the Precedence for this Password Policy then click “Nextâ€.
Note: This is used if a users has multiple Password Settings Object (PSO) applied to them.
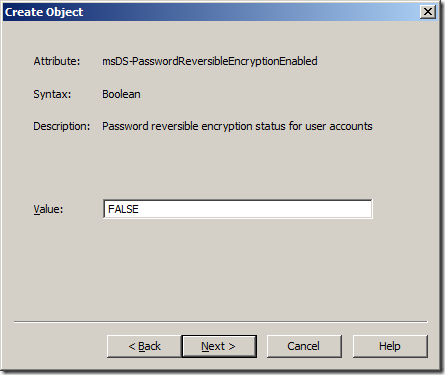
Step 7. Type “FALSE†in the value field and click “Nextâ€
Note: You should almost never use “TRUE†for this setting.
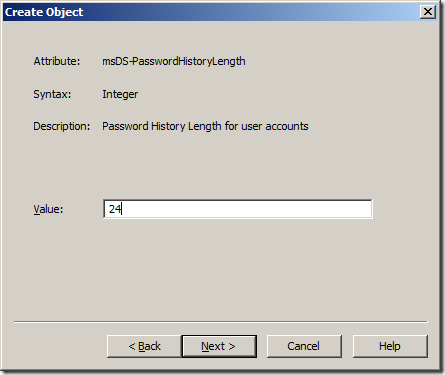
Step 8. Type “24†in the “Value†field and click “Nextâ€
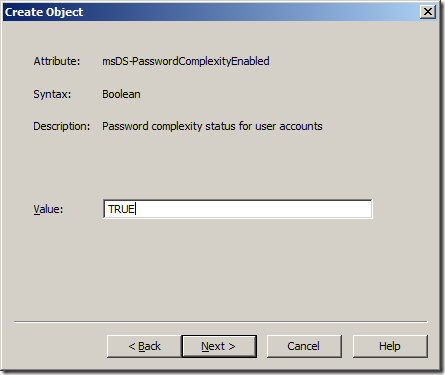
Step 9. Type “TRUE†in the “Value†field and click “Nextâ€
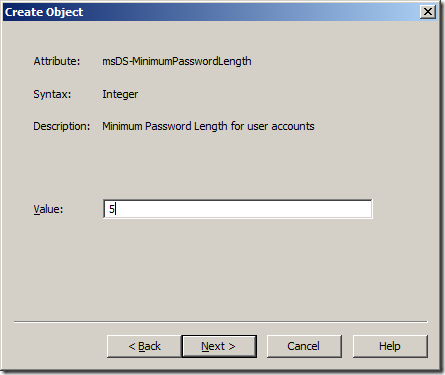
Step 10. Type “5†in the “Value†field and click “Nextâ€
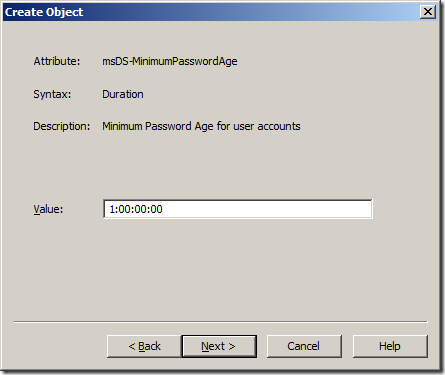
Step 11. Type “1:00:00:00†in the “Value†field and click “Nextâ€
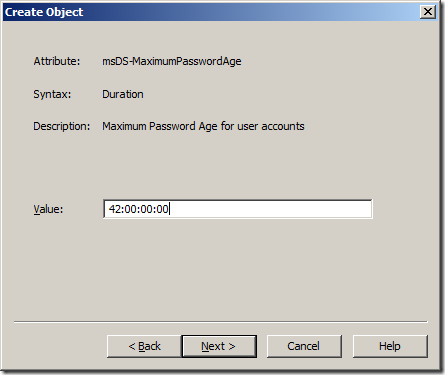
Step 12. Type “42:00:00:00†in the “Value†field and click “Nextâ€
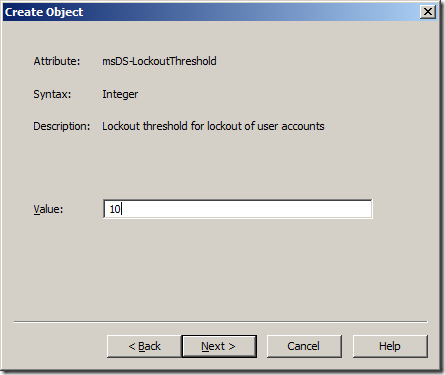
Step 13. Type “10†in the “Value†field and click “Nextâ€
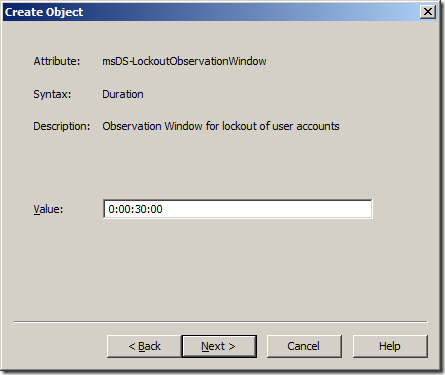
Step 14. Type “0:00:30:00†field and click “Nextâ€
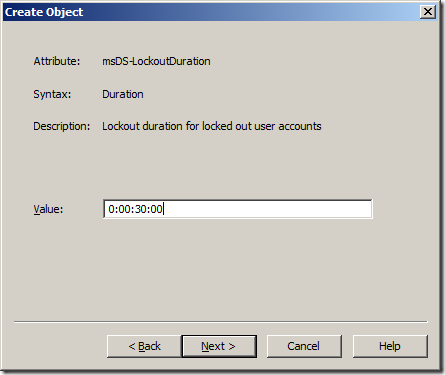
Step 15. Type “0:00:33:00†in the “Value†field and click “Nextâ€
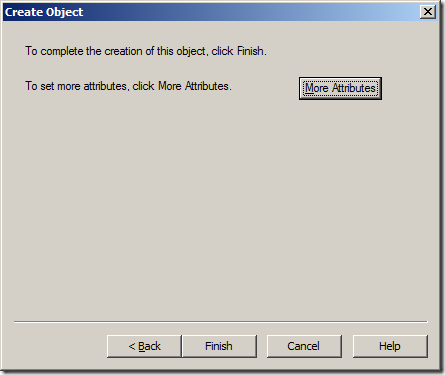
Step 16. Click “Finishâ€
You have now created the Password Settings Object (PSO) and you can close the ADSIEdit tool.
Now to apply the PSO to a users or group…
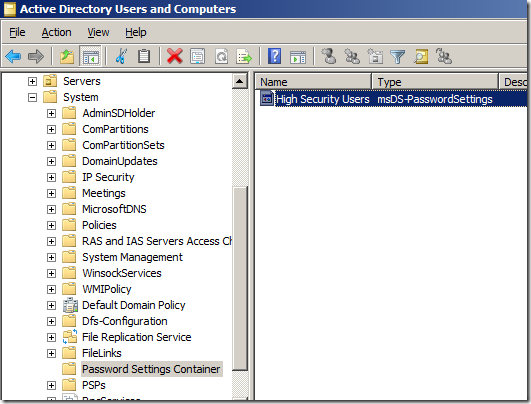
Step 17. Open Active Directory Users and Computers and navigate to “System > Password Settings Containerâ€
Note: Advanced Mode needs to be enabled.
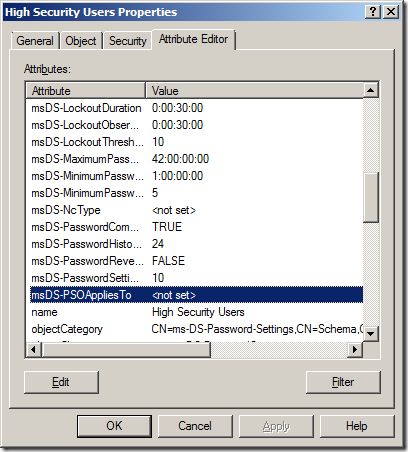
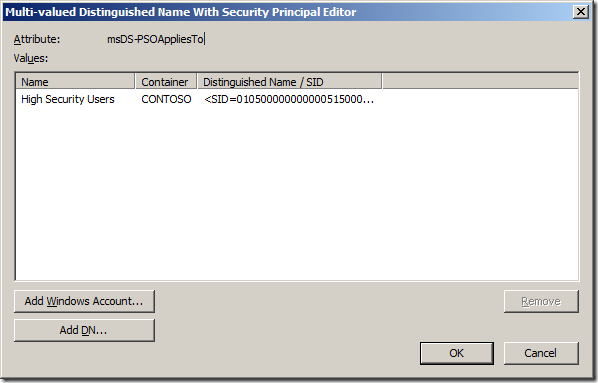
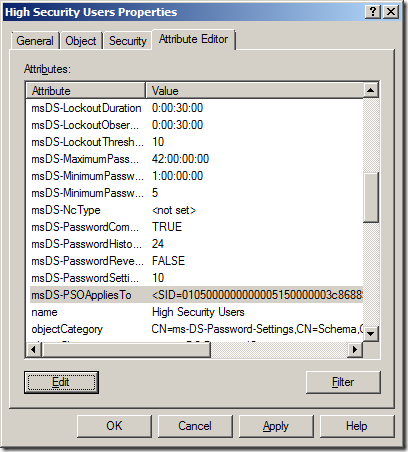
Step 18. Double click on the PSO you created then click on the “Attribute Editor†tab and then select the “msDS-PSOAppliedTo†attribute and click “Editâ€
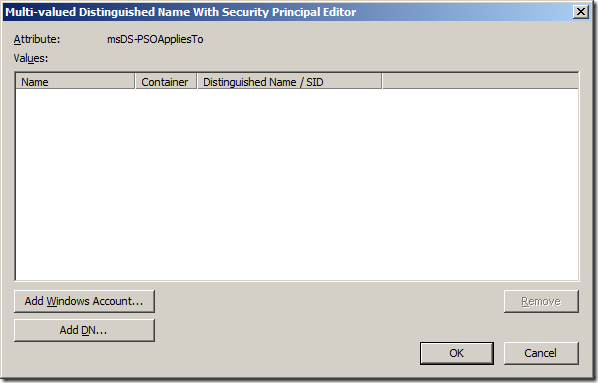
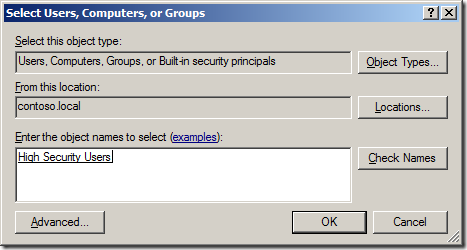
Step 19. Click “Add Windows Accounts….†button.
Step 20. Select the user or group you want to apply this PSO and click “OKâ€
Step 21. Click “OKâ€
Step 22. Click “OKâ€
And your are done… (told you it was hard).
Other Useful Links
AD DS: Fine-Grained Password Policies
AD DS Fine-Grained Password and Account Lockout Policy Step-by-Step Guide




Blog Post: Tutorial: How to setup Default and Fine Grain Password Policy http://bit.ly/ohuT5C
Blog Post: Tutorial: How to setup Default and Fine Grain Password Policy http://bit.ly/ohuT5C
Blog Post: Tutorial: How to setup Default and Fine Grain Password Policy http://bit.ly/ohuT5C
Tutorial: How to setup Default and Fine Grain Password Policy http://feedproxy.google.com/~r/GroupPolicyCenter/~3/B8Zt13h0Ehg/
Tutorial: How to setup Default and Fine Grain Password Policy http://t.co/O2vNV0I via @alanburchill
Very useful Tutorial. In many other tutorials I did not see anything regarding the “Default Domain Policy”..so I think your article is better 🙂
Thank you very much !
I just wanted to say thank you for the great post. I really liked steps 18-20. These steps are much easier than dealing with the LDAP DN syntax.
IS it compulsory to do this functional level windows 2008 ???
or Is it possible to do in Windows 2003 functional Level???
Must be 2008 mode…
I am curious. I carefully ran through the settings, really only changing the password length to 8, the password age to 75, and the lockout threshold to 7, keeping all others at the default. When I logon as a user assigned to the security group, I get an “Access Denied” message. I set the password precedence setting to 10, although this is the first custom PSO I am designing. I am at a 2008 R2 Domain Level.
I am curious. I carefully ran through the settings, really only changing the password length to 8, the password age to 75, and the lockout threshold to 7, keeping all others at the default. When I logon as a user assigned to the security group, I get an “Access Denied†message *when I try to change the password*. I set the password precedence setting to 10, although this is the first custom PSO I am designing. I am at a 2008 R2 Domain Level.
I apologize for the last message. It appears the test account had the password set to “User cannot change password.” Once that was corrected I found that although I am still having problems getting a group to be associated with the PSO, individual users work fine.
Group membership can take 8 hours to apply if you do not reboot/logoff….
updated link for Jorge’s blog is: http://jorgequestforknowledge.wordpress.com/2008/12/16/why-gpos-with-password-and-account-lockout-policy-settings-must-be-linked-to-the-ad-domain-object-to-be-affective-on-ad-domain-user-accounts/
Great article.. Question: GPO for password complexity is disabled and users create passwords. Password complexity will be enabled after a while, will every user have to change the password or only the ones with a non-complex password?
Awesome. Thanks a lot!
Hi,
Thank you for the wonderful article. How to query or validate whether the FGP policy is applied successfully to users/OU level.
Priyasam
Great article! let me know how to configure password policies through powershell? is it possible?
Absolutely brilliant – I’ve often wondered where all the good documentation is – and now I’ve found some! 🙂 Made my life simples – thanks a lot 🙂
Helo ALl,
Can we apply multiple password policy on the GPO, ex OU Specific.
and what is the Different between apply Password policy for Domain Controllers Policy and Default domain Policy.
Thank you! This got me started on the project. I should mention for permanent LockoutDuration the value “(never)” including parenthesis may be used. Also your link for Shadow Groups was invalid, but there are some good sources to be found.
Awesome blog…
Good article. But I have one question.
Suppose that my domain has complex password policy applied at domain level and I create a relaxed password complexity PSO and add it to one of the groups.
Now how can I directly create a user that follows the relaxed password policy? Is it like I need to create a user, first with complex password, them move it to the respective group and then again set the password to relaxed one?
Please provide some further guidance.
Thanks
Good article. But I have one question.
Suppose that my domain has complex password policy applied at domain level and I create a relaxed password complexity PSO and add it to one of the groups.
Now how can I directly create a user that follows the relaxed password policy? Is it like I need to create a user, first with complex password, then move it to the respective group and then again set the password to relaxed one?
Please provide some further guidance.
Thanks
You are correct… you first need to create the user and then add them to the group. So you user provisioning process will need to add the user to the group immediatly after the account is created.
Hello, I changed the default password policy default domain policy of WindowsServer2012R2. I now want to restore it to the default group policy configuration. Now the AD organizational unit and user usage cannot be affected in any way. Can this be done?