![]() This article will show you how to disabled SSL v2 and SSL v3 on browsers on the client using Group Policy. SSL v2 and SSL v3 protocols for a long time has been considered to be broken protocols thanks to the many vulnerabilities found in these protocols like BEAST and POODLE to name but a few. While all newer browsers no longer have these protocols supports enabled by default you still might be But many web sites sill support these protocols due to legacy configuration. Therefore it’s still a good idea to turn off these protocols on the web browsers so that clients are never forced into using these old and insecure protocols.
This article will show you how to disabled SSL v2 and SSL v3 on browsers on the client using Group Policy. SSL v2 and SSL v3 protocols for a long time has been considered to be broken protocols thanks to the many vulnerabilities found in these protocols like BEAST and POODLE to name but a few. While all newer browsers no longer have these protocols supports enabled by default you still might be But many web sites sill support these protocols due to legacy configuration. Therefore it’s still a good idea to turn off these protocols on the web browsers so that clients are never forced into using these old and insecure protocols.
It should be noted that while I say that this is a for browsers on the client these settings should be applied to all windows computers in your organisation whether they are servers or workstations. Now I would ALWAYS say that using a web browser on a server is a bad idea, in fact it should be blocked. However, just be realistic some admins can and do from time to time use browsers on servers meaning its still important to implement this lockdown on all your windows computers.
Also, in case you were confused, SSL and TLS are pretty much the same thing. Just think of TLS 1.0 as SSL v4 and so on. Most people still think SSL when they see that padlock in the address bar, it just that mostly it is now secured using the TLS protocols.
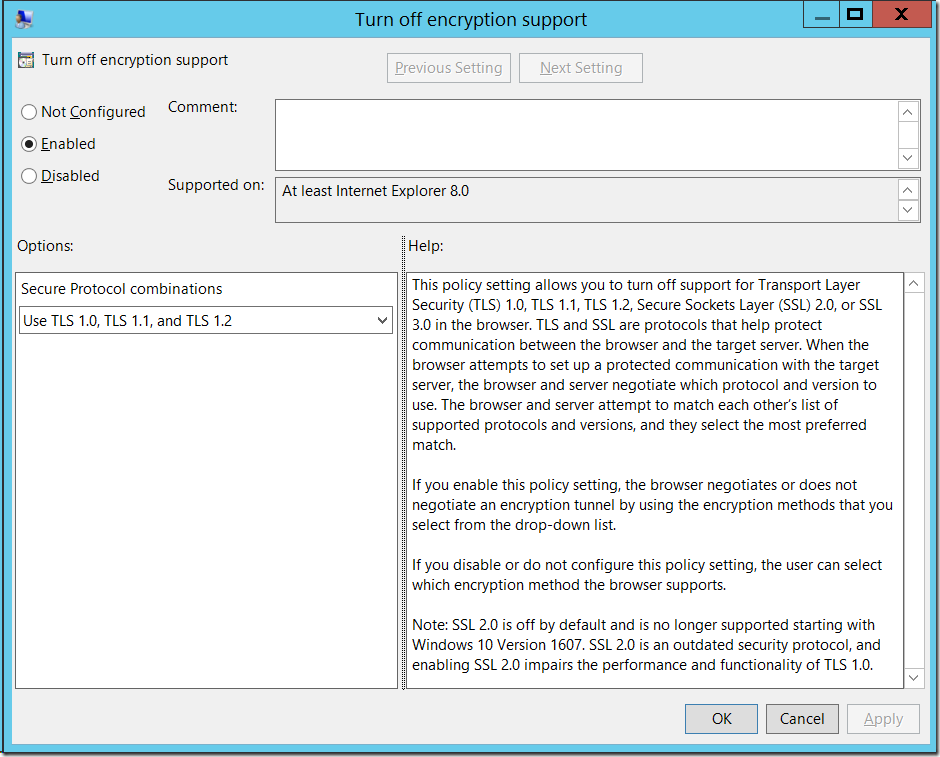
To disable SSL v2 and SSL v3 its best to create a Computer based Group Policy settings that applies at the top level of your domain. In GPMC navigate to Computers Configuration > Policies > Administrative Templates > Windows Components > Internet Explore > Internet Control Panel > Advanced Page and then open the policy setting called “Turn off encryption supportâ€.
Once you have the policy open you will notice there is a drop down option that will give you 32 different permutation of having enabled or disabling SSL and TLS.
Generally most sites on the Internet with encryption support TLS 1.0 or later. So the best bet would be to select the option “Use TLS 1.0, TLS 1.1, and TLS 1.2â€.
In case you were wondering, yes, this will break any site for your users that only uses SSL v3 or earlier. But its probably best that you don’t use those site as they either don’t care or don’t understand about security.
However, if you do have a any site that your users absolutely must access that still uses SSL v3 then you can still exclude the computer from the policy by following my other blog post at https://www.grouppolicy.biz/2010/05/how-to-exclude-individual-users-or-computers-from-a-group-policy-object/ .
Now that you have disable SSL on your client the next thing to look at is disabling the protocol on all you internal (and external servers). In my next post I will show you how to also disable SSL (and enabled TLS 2.0) on all your servers using Group Policy.